
Set up your ASA easily. When you finish your former big two steps “Connecting PC to ASA” and “Installing ASDM”. Follow the third step “Configuring ASA”.
Configuring ASA
1. Launching ASDM
Now you can launch the Cisco ASDM with the Cisco ASDM Launcher.
Step1. Click [OK.] Leave the username and password fields empty. The Security warning appears.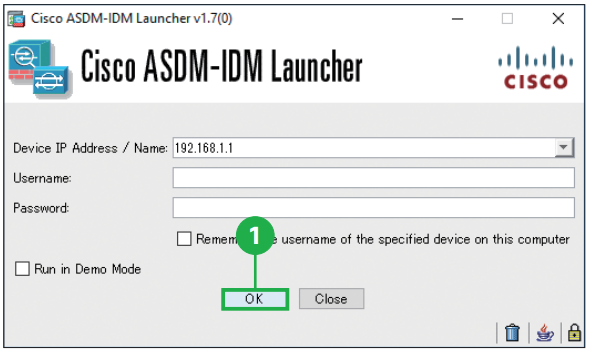 Step2. Click [Continue].
Step2. Click [Continue].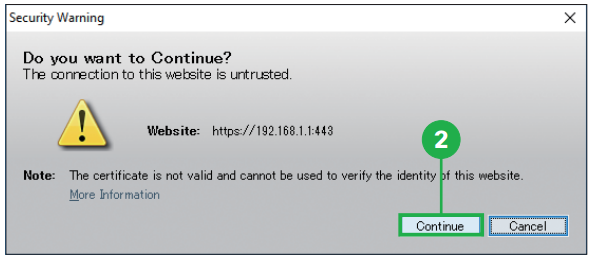 Step3. Click [Cancel]. The main ASDM window appears.
Step3. Click [Cancel]. The main ASDM window appears.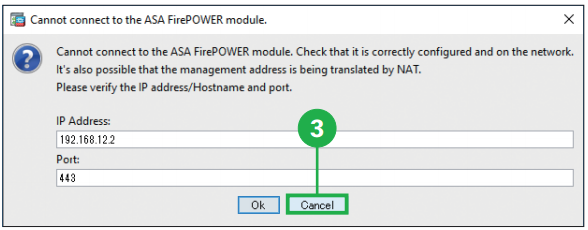 MEMO: At step3, you are prompted to provide the IP address of the ASA Firepower module. You can later set the module IP address to the correct IP address using the Startup Wizard.
MEMO: At step3, you are prompted to provide the IP address of the ASA Firepower module. You can later set the module IP address to the correct IP address using the Startup Wizard.
2. Launching Startup Wizard
After launching ASDM, use the Startup Wizard to perform initial configuration.
Step1. Click [Startup Wizard] from the [Wizards] menu bar.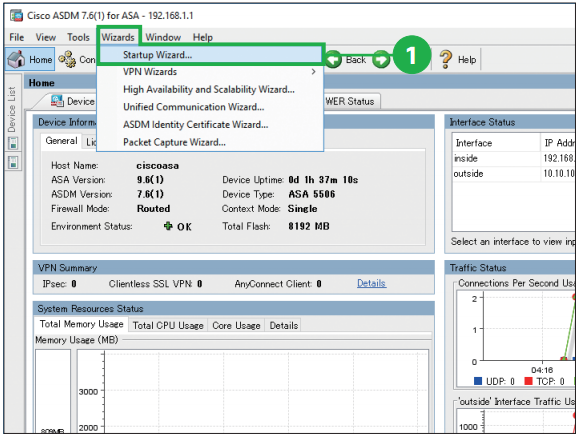 Step2. Click [Modify existing configuration].
Step2. Click [Modify existing configuration].
Step3. Click [Next].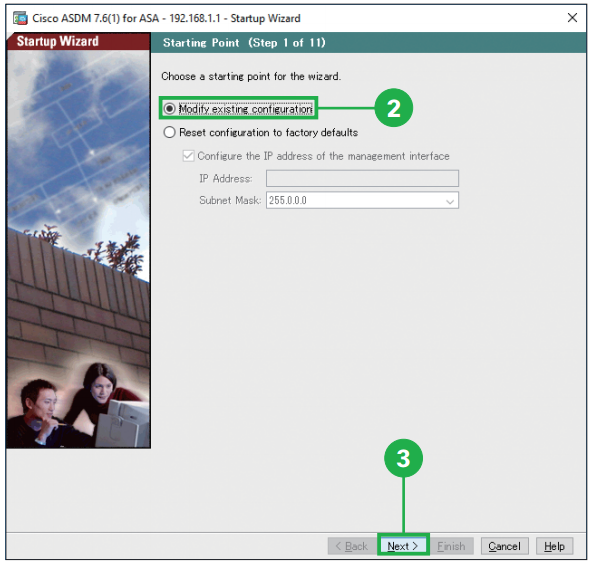 Step4. Click [Next]. You can enter the host name and the domain name of the ASA.
Step4. Click [Next]. You can enter the host name and the domain name of the ASA.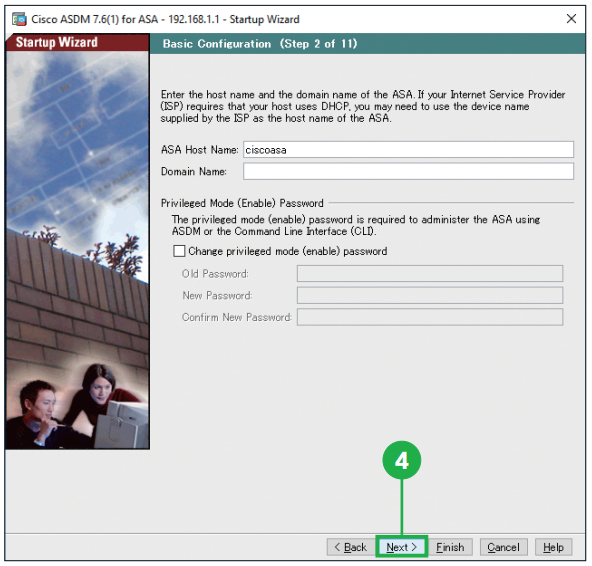 Step5. Select the appropriate option. Configure the outside interface of the ASA. If you use the ASA “behind” the existing router, select [Use DHCP] in most cases. If you use the ASA “instead of” the existing router, follow the configuration of the router.
Step5. Select the appropriate option. Configure the outside interface of the ASA. If you use the ASA “behind” the existing router, select [Use DHCP] in most cases. If you use the ASA “instead of” the existing router, follow the configuration of the router.
Step6. Click [Next].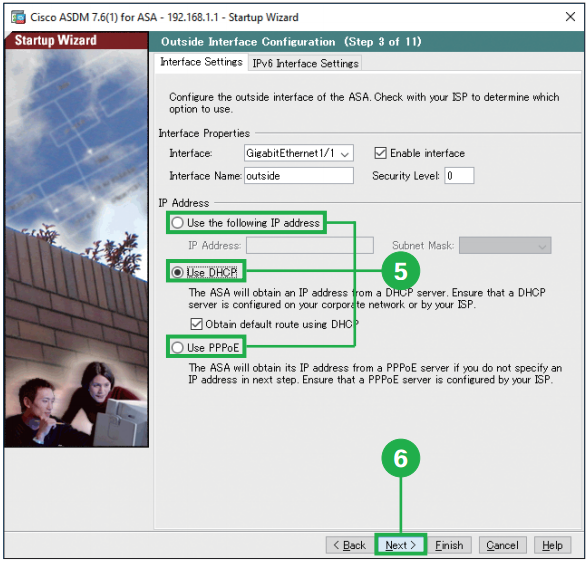 Step7. Click [Next].
Step7. Click [Next].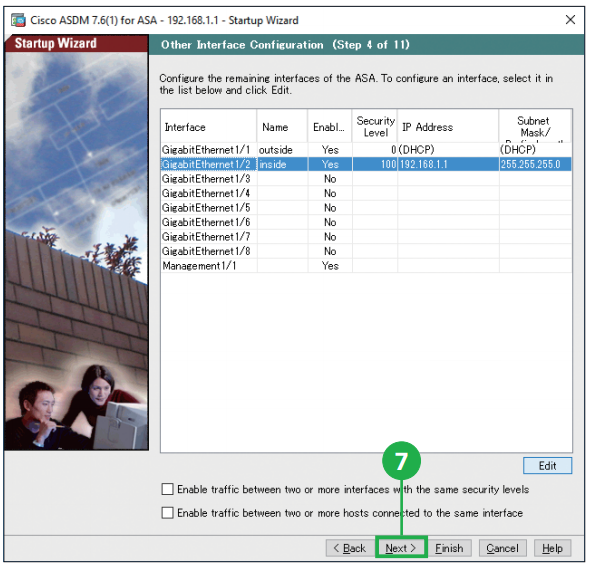 Caution: To the inside interfaces, you must assign the range of IP addresses different from the range assigned to the outside interface. For example, if the outside range is 192.168.1.x, the inside range should be 192.168.10.x, and so on. You can change the range by selecting an interface and clicking [Edit].
Caution: To the inside interfaces, you must assign the range of IP addresses different from the range assigned to the outside interface. For example, if the outside range is 192.168.1.x, the inside range should be 192.168.10.x, and so on. You can change the range by selecting an interface and clicking [Edit].
Step8. Click [Next]. You can specify static routes if your network has multiple routers.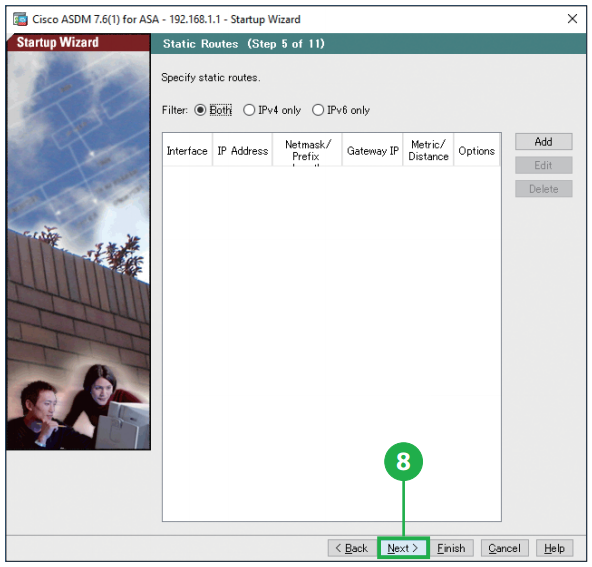 Step9. Click [Next]. The ASA can act as a DHCP server and provide IP addresses to the hosts on your inside network.
Step9. Click [Next]. The ASA can act as a DHCP server and provide IP addresses to the hosts on your inside network.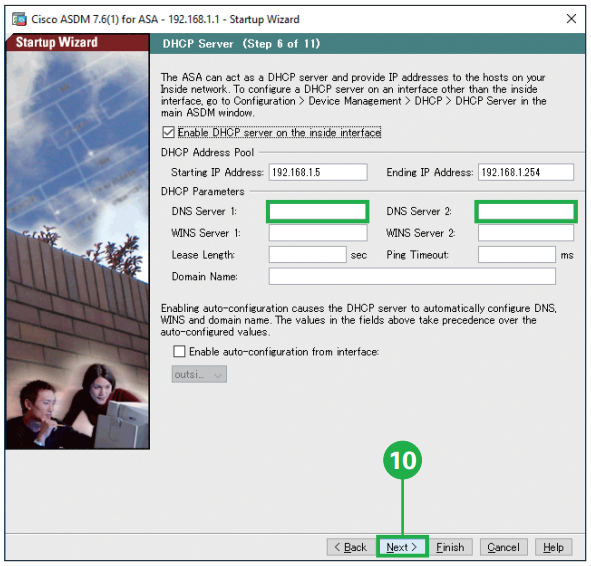 MEMO: To connect to the free and fast Cisco Umbrella global net – work DNS service, enter the “208.67.222.222” in the [DNS Server 1] field and the “208.67.220.220” in the [DNS Server 2] field.
MEMO: To connect to the free and fast Cisco Umbrella global net – work DNS service, enter the “208.67.222.222” in the [DNS Server 1] field and the “208.67.220.220” in the [DNS Server 2] field.
Step10. Click [Use Port Address Translation (PAT)]. Select [Use Port Address Translation (PAT)] to share a single external IP address for devices on the inside interface. Select [Use Network Address Translation (NAT)] to share several external IP address for devices on the inside interface.
Step11. Click [Next].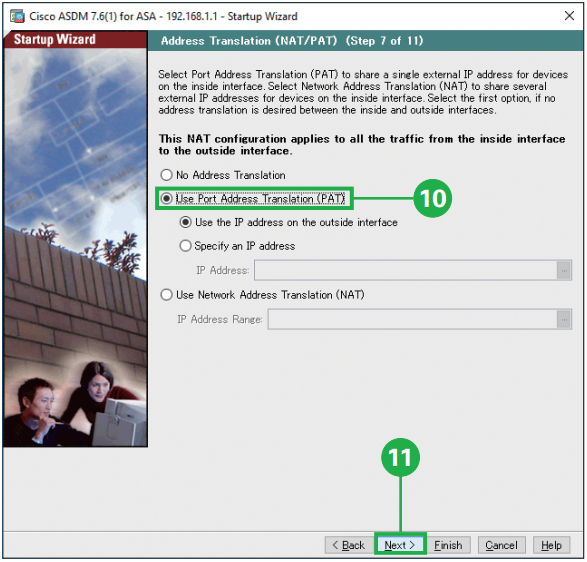 Step12. Click [Next]. You can specify the addresses of all hosts or networks, which are allowed to access the ASA using HTTPS/ASDM, SSH or Telnet.
Step12. Click [Next]. You can specify the addresses of all hosts or networks, which are allowed to access the ASA using HTTPS/ASDM, SSH or Telnet.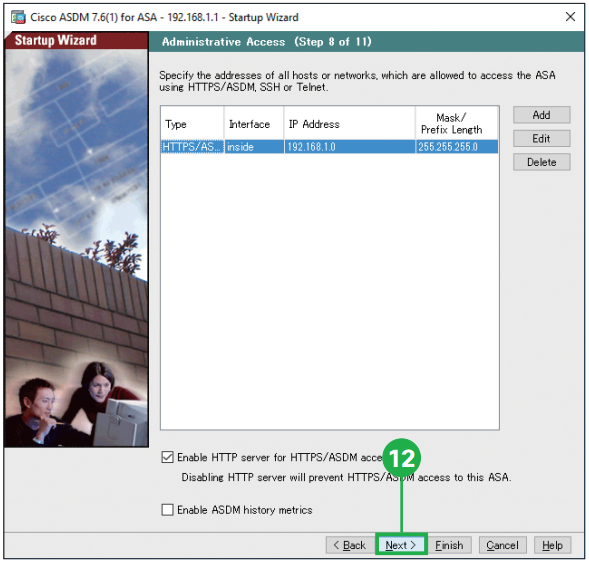 Step13. Enter the IP address for the ASA Firepower module. For example, the “192.168.1.2” works with the default configuration.
Step13. Enter the IP address for the ASA Firepower module. For example, the “192.168.1.2” works with the default configuration.
Step14. Enter the IP address of the Default Gateway. For example, the “192.168.1.1” works with the default configuration.
Step15. Click [Next].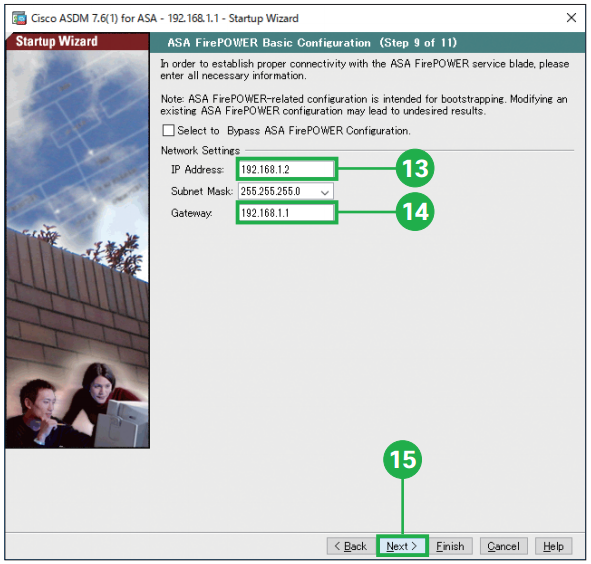 Step16. Click [Next]. The ASA can be remotely managed from an Auto Update Server. This includes automatic updating the ASA configuration, ASA image, ASDM image as needed.
Step16. Click [Next]. The ASA can be remotely managed from an Auto Update Server. This includes automatic updating the ASA configuration, ASA image, ASDM image as needed.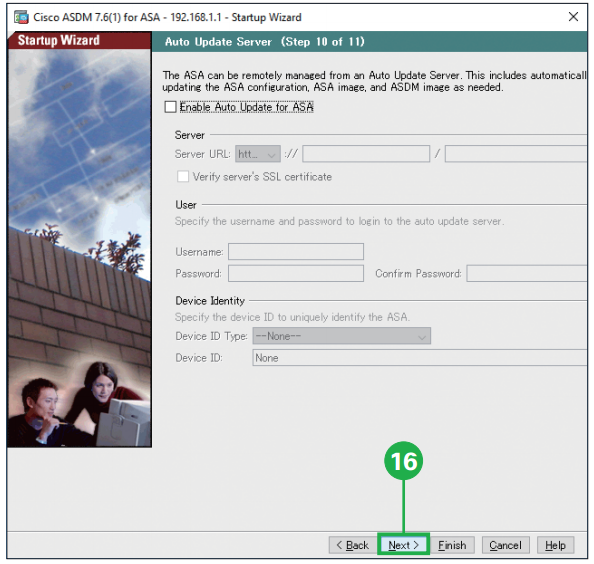 Step17. Click [Finish]. You have completed the Startup Wizard. To send your changes to the ASA, click [Finish]. If you want to modify any of the data, click [Back].
Step17. Click [Finish]. You have completed the Startup Wizard. To send your changes to the ASA, click [Finish]. If you want to modify any of the data, click [Back].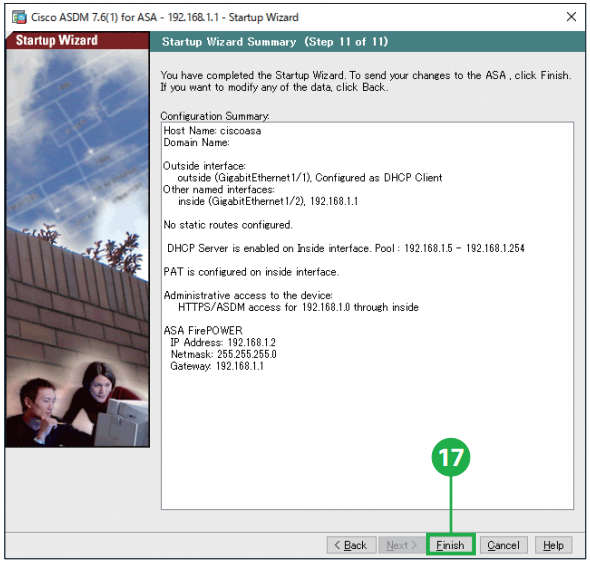
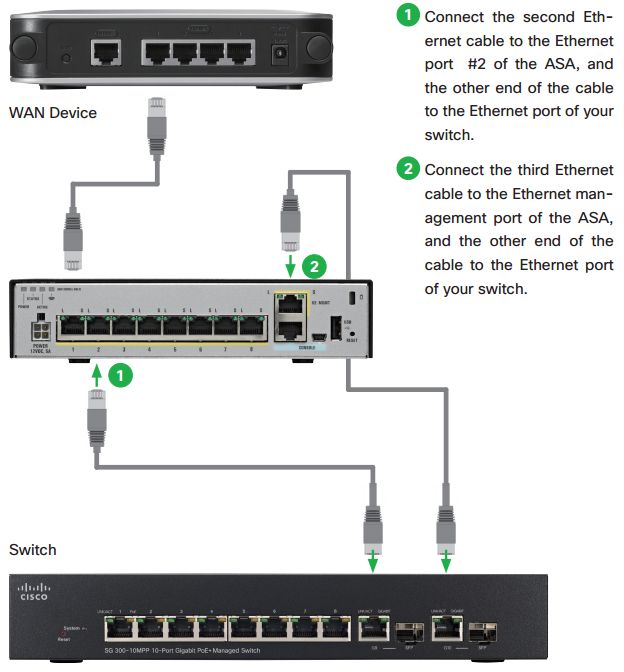
3. Connecting Switch to ASA
After completing the Startup Wizard, exit the ASDM and disconnect the Ethernet cable from your PC. Then, follow these steps to connect your switch to the ASA. Make sure that nothing is connected to the switch, its settings are configured to use DHCP, and the first Ethernet cable is still connected between the ASA and your WAN device.
4. Install Licenses
Now you can access to the ASA Firepower module with the Cisco ASDM. Relaunch the Cisco ASDM and install the licenses. The Control and Protection licenses are provided by default and the Product Authorization Key (PAK) is included on a printout in your box. If you ordered additional licenses, you should have PAKs for those licenses in your email.
Step1. Launch ASDM and Click [Configuration].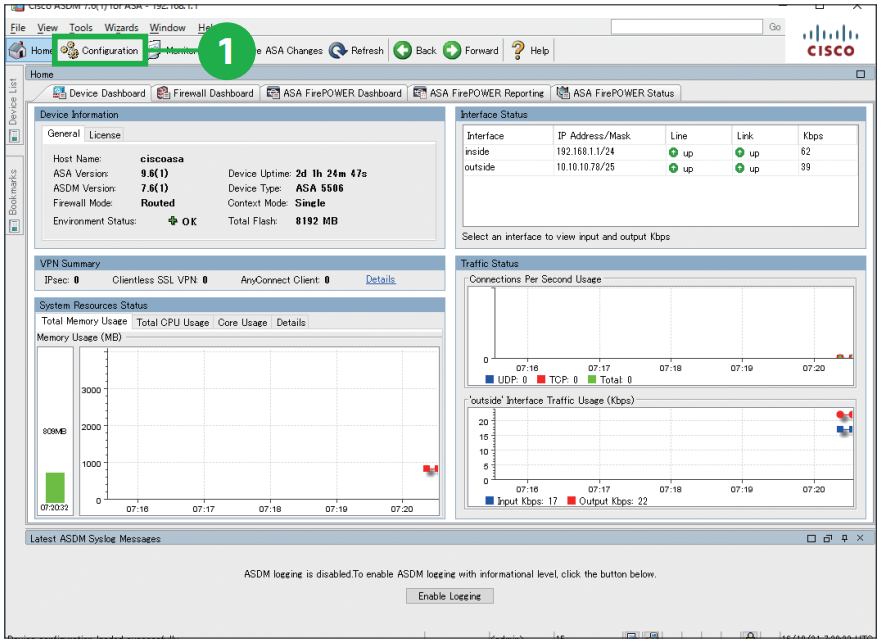
MEMO: The Cisco ASA with Firepower Services ship with a base license for Application Visibility and Control (AVC). Optional subscriptions for Next-Generation IPS (NGIPS), Cisco Advanced Malware Protection (AMP), and URL Filtering (URL) can be added to the base configuration for advanced functionality.
- AVC: Supports more than 3,000 application-layer and risk-based controls that can launch tailored intrusion prevention system (IPS) threat detection policies to optimize security effectiveness.
- NGIPS: Provides highly effective threat prevention and full contextual awareness of users, infrastructure, applications, and content to detect multifactor threats and automate defense response.
- AMP: Delivers inline network protection against sophisticated malware and Cisco Threat Grid sandboxing.
- URL: Adds the capability to filter more than 280 million top-level domains by risk level and more than 82 categories.
Step2. Click [ASA FirePOWER Configuration].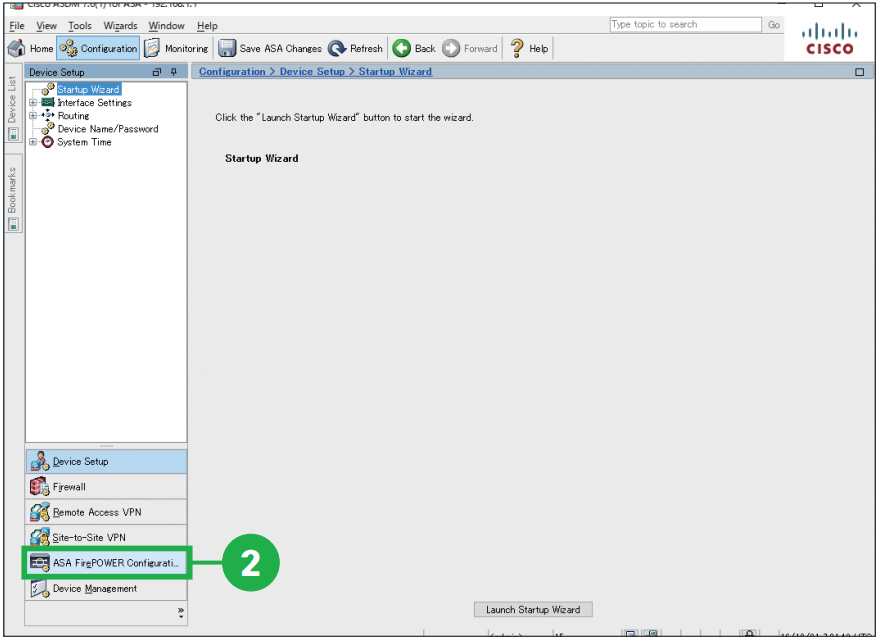 Step3. Click [Licenses].
Step3. Click [Licenses].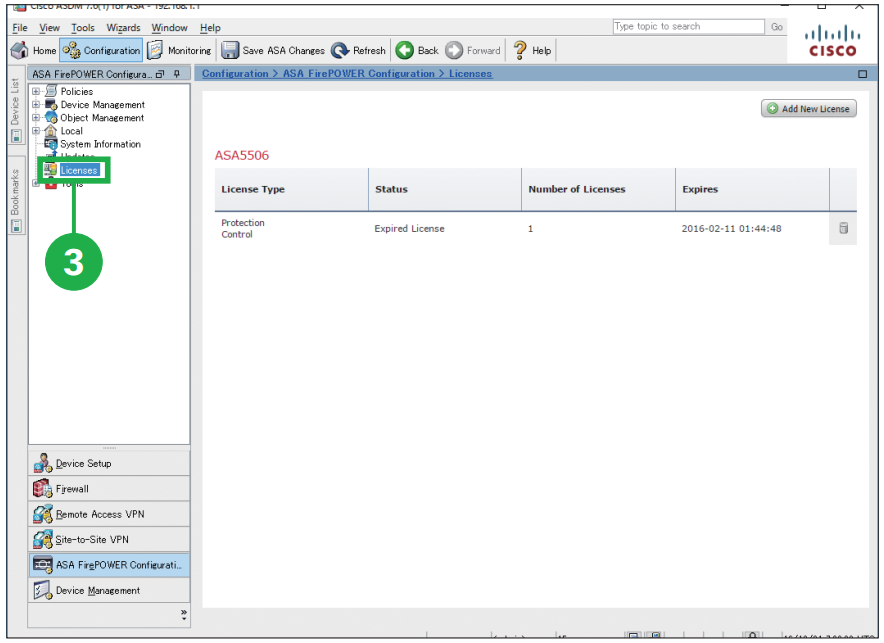 Step4. Copy [License Key] text and get the license from the licensing portal (see the MEMO in the next page).
Step4. Copy [License Key] text and get the license from the licensing portal (see the MEMO in the next page).
The example of the License Key is 72:78:DA:6E:D9:93:35.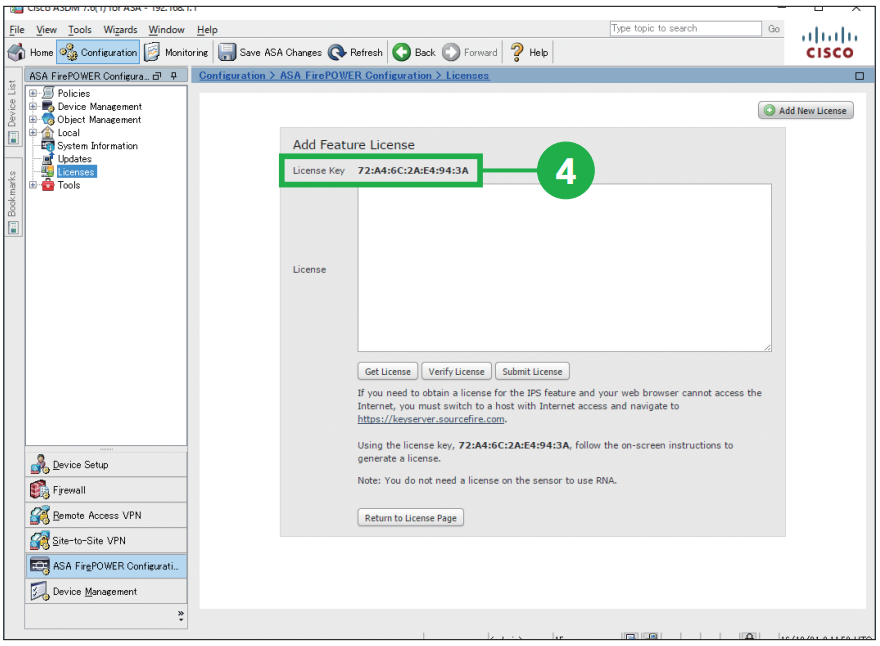 Step5. Paste the license activation key into [License] box.
Step5. Paste the license activation key into [License] box.
Step6. Click [Verify License].
Step7. Click [Submit License].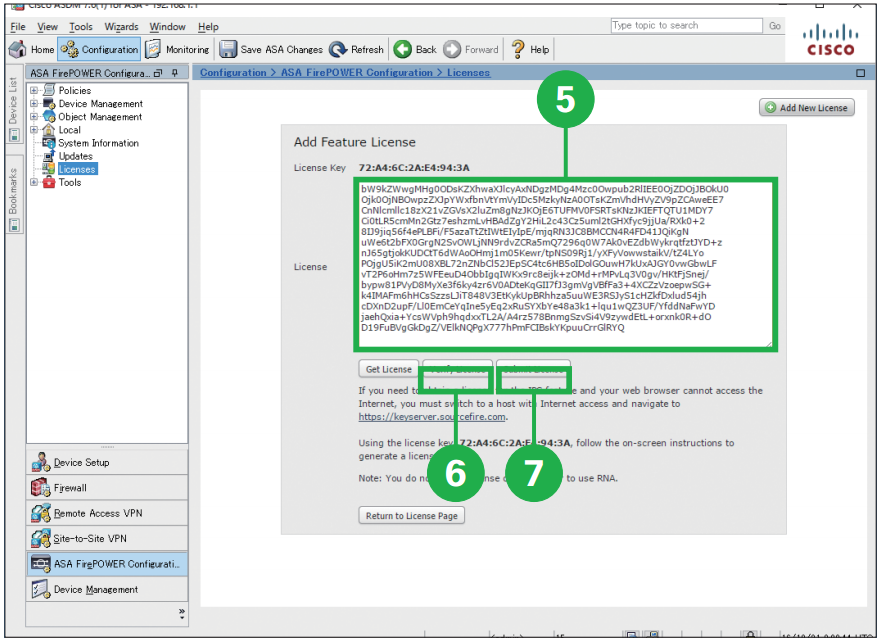 Step8. If you have additional licenses, click [Add New License] and repeat the steps 5 to 7.
Step8. If you have additional licenses, click [Add New License] and repeat the steps 5 to 7.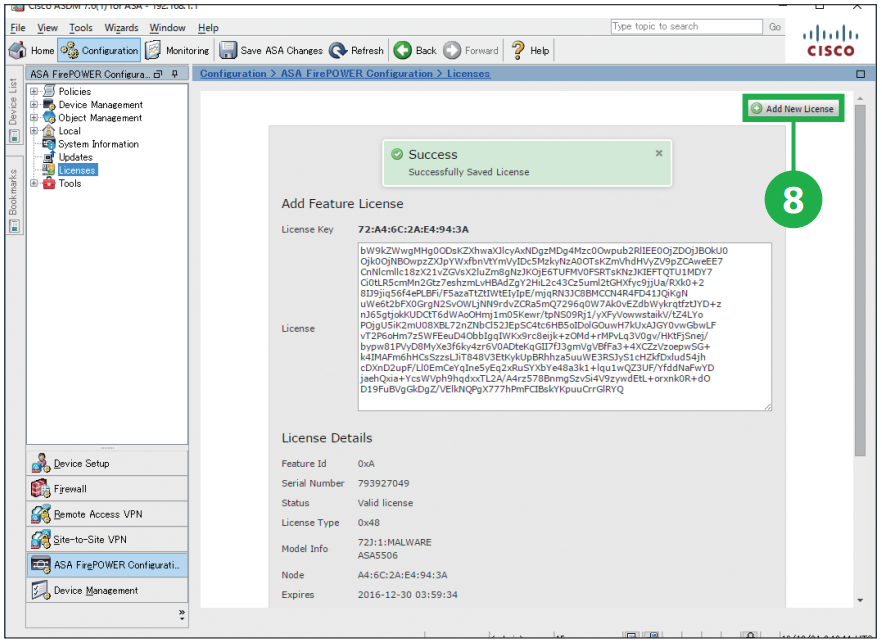 MEMO: You can get the license (license activation key) from the licensing portal.
MEMO: You can get the license (license activation key) from the licensing portal.
- Go to https://www.cisco.com/go/license.
- Enter the PAKs separated by commas in the Get New Licenses field, and click Fulfill.
- You will be asked for the License Key and email address among other fields.
- Copy the resulting license activation key from either the website display or from the zip file attached to the licensing email that the system automatically delivers.
More related
Cisco ASA with Firepower Services, Setup Guide-Part1
Cisco ASA with Firepower Services, Setup Guide-Part2
Cisco ASA with Firepower Services, Setup Guide-Part4
How to Deploy the Cisco ASA FirePOWER Services in the Internet Edge, VPN Scenarios and Data Center?


