We talked about the new models of Cisco ASA with FirePOWER services: the ASA 5508-X and 5516-X.
The new ASA 5508-X and 5516-X provide midsize companies, branch offices and industrial environments with the same advanced malware protection and threat detection capabilities deployed by large enterprise organizations. (5508-X and 5516-X–1RU threat centric NGFW for branch offices and midsize businesses)
Yes, with the cool ASA 5508-X or 5516-X, you can set a better network. So how to deploy the ASA 5508-X or ASA 5516-X in your network? We will tell you in this article.
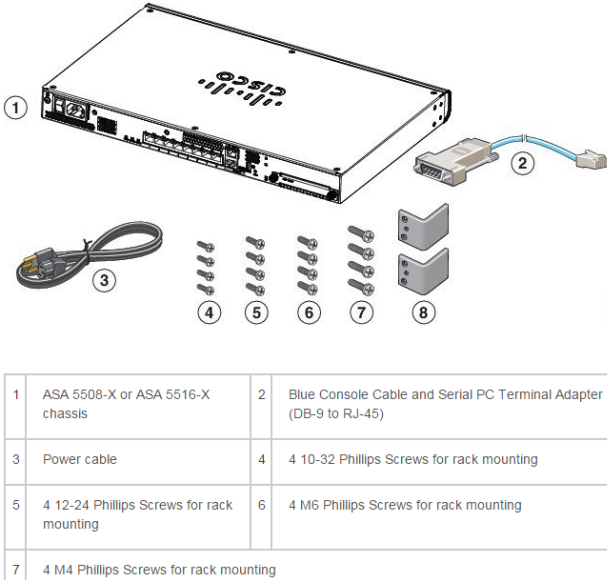
Firstly, let’s have a look at the package contents of the chassis.
Note: The contents are subject to change, and your exact contents might contain additional or fewer items.
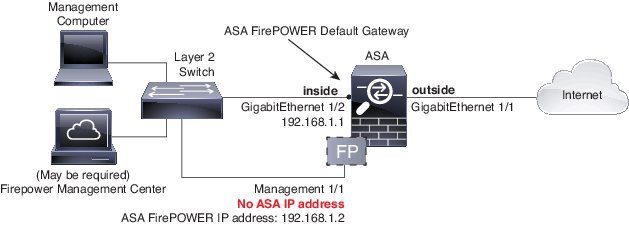
How to deploy the ASA 5508-X or ASA 5516-X in Your Network? You can read the following figure shows the recommended network deployment for the ASA 5508-X or ASA 5516-X with the ASA FirePOWER module:
Note: You must use a separate inside switch in your deployment.
The default configuration enables the above network deployment with the following behavior.
■ inside–> outside traffic flow
■ outside IP address from DHCP
■ DHCP for clients on inside
■ Management 1/1 belongs to the ASA Firepower module. The interface is Up, but otherwise unconfigured on the ASA. The ASA Firepower module can then use this interface to access the ASA inside network and use the inside interface as the gateway to the Internet.
Note: Do not configure an IP address for this interface in the ASA configuration. Only configure an IP address in the Firepower configuration. You should consider this interface as completely separate from the ASA in terms of routing.
■ ASDM access on the inside interface
Note: If you want to deploy a separate router on the inside network, then you can route between management and inside. In this case, you can manage both the ASA and ASA FirePOWER module on Management 1/1 with the appropriate configuration changes.
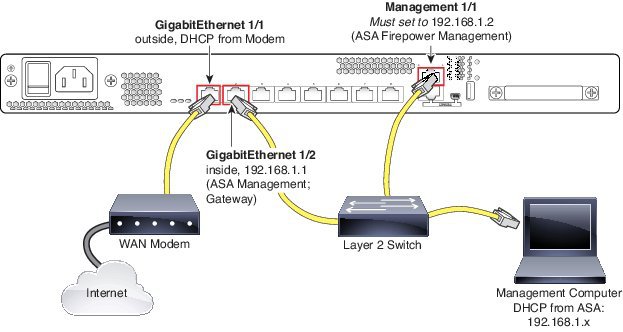
Procedure to Deploy the ASA 5508-X or ASA 5516-X
1. Cable the following to a Layer 2 Ethernet switch:
- –GigabitEthernet 1/2 interface (inside)
- –Management 1/1 interface (for the ASA Firepower module)
- –Your computer
Note: You can connect inside and management on the same network because the management interface acts like a separate device that belongs only to the ASA Firepower module.
2. Connect the GigabitEthernet 1/1 (outside) interface to your WAN device, for example, your cable modem.
Note: If the cable modem supplies an outside IP address that is on 192.168.1.0/24, then you must change the ASA configuration to use a different IP address.
…
More related information about the Cisco ASA 5508-X and ASA 5516-X such as Power on the ASA, Launch ASDM, and Configure the ASA FirePOWER Module, etc. you can read the full document
More Related
Cisco ASA 5500-X Series’ New Features & Main Model Comparison
What are the Considerations While Buying a Cisco Next-Generation Firewall?
NGFW-Cisco ASA with FirePOWER Services
ASA 5506-X/SecurityPlus, 5506W-X & 5506H-X, Cisco ASA with FirePOWER Services, What’s New Here?
The New Cisco ASA 5506-X, More Comparisons
How to Start a Cisco ASA 5506-X?