
In what scenario would you use an ASA in transparent mode? Transparent mode is defined as both inside and outside interfaces are in the same subnet, but different VLAN’s….
Uh huh, let’s say that you and I have a customer that wants to add a firewall to their network.
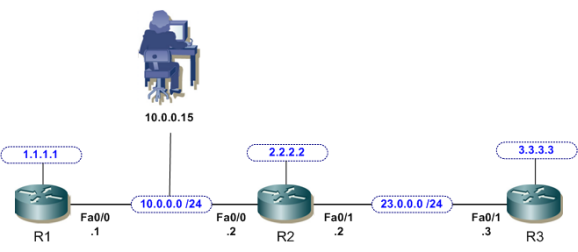
If we put the firewall in at L3, between R1 and R2, we would have to do some IP re-addressing, as each L3 interface on the ASA would be a different subnet, and R1 and R2 are currently on the same subnet.
If we choose to use L2 (transparent firewall) implementation, then we could do this:
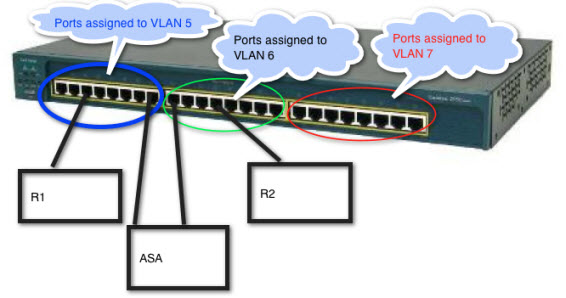
From the switch, VLAN5 and VLAN 6 are 2 separate VLANs, but if the ASA is in transparent mode, the ASA will bridge those 2 together into a single L2 broadcast domain.
All the devices in VLANs 5 and 6 would use the same L3 network address space, but all the traffic between R1 and R2 would go through the ASA in transparent mode.
Q Discussion from https://learningnetwork.cisco.com/thread/44299
More Comments:
I would use an ASA in transparent mode when I needed to do firewalling at layer 2. In other words, if I had some hosts on a broadcast domain that I wanted to control in regards to their communications to other hosts on the same broadcast domain. In general, transparent mode keeps you from having to re-address your hosts.
So can we use an ASA to do private vlans then? In fact, not technically. We can use it to bridge two broadcast domains (just as you old with a cable). That’s not really PVlan. PVLAN has three strict categories–promiscuous, community and isolated. You can’t really further restrict or unrestricted within the PVlan ecosystem. On the other hand, ASA transparent gives you lots of flexibility to allow and deny traffic through the device. However, there are only two groups of devices connected to an ASA in transparent mode (devices in the first port and devices on the second port). Devices within each group would communicate unrestricted because the design does not force them through the ASA. Devices communicating with the opposing group would send traffic through the ASA. We could use PVLANs in conjunction with ASA transparent mode, but they are different concepts.
Another caveat is that the ASA5505 supports PVLAN edge in its integrated switch. This is implemented with ‘switch port protected’. Any two ports in the same vlan configured that way cannot communicate at layer 2. Sort of a lite version of PVLAN that only works in a single device.
What’s your opinion? Go ahead…
More Related Cisco ASA Topics:


