
In order to design and implement Cisco Wireless solutions successfully, CCNA Wireless students need to be familiar with the options for various wireless topologies. Two were defined by the 802.11 committees, while others were made possible thanks to excellent developments by wireless vendors like Cisco Systems. How many types of wireless network? What is the exact Wireless Topologies? Let’s share the detailed illustrations that was written by Jerome Henry from Ciscopress.com
Main Wireless Network Types
Wireless networks use different technologies depending on the distance to achieve, the number of devices to connect, and the amount of information to transmit. The technologies include
- Wireless personal-area networks (WPAN): Have a short range (up to 20–30 feet/7–10 meters), commonly use the 802.15 family of specifications to connect two or a few devices with low power consumption. Bluetooth is an example of WPAN protocol.
- Wireless local-area networks (WLAN): Consume more power but extend the connection to about 300 feet (100 meters). WLANs are the main topic of this book.
- Wireless metropolitan-area network (WMAN): Extend the range to a larger geographic area, such as a city or suburb. Applications vary from point-to-point or point-to-multipoint links to multiuser coverage. WMANs typically use licensed frequencies (a fee has to be paid for permission to use the frequency), although implementations in the ISM bands can also be found. WiMAX is an example of WMAN protocol (most WiMAX implementations use licensed bands).
- Wireless wide-area network (WWAN): Provide connectivity over a wide geographical area. Usually, WWANs are networks used for mobile phone and data service and are operated by carriers. WWANs typically use licensed frequencies.
Wireless Topologies
Two wireless devices in range of each other just need to share a common set of simple parameters (frequency and so on) to be able to communicate and establish a WLAN. A first station defines the radio parameters and a connection name; the other stations just need to detect the connection and adjust their own parameters to connect to the first station and to each other. This is called an ad hoc network.
As soon as wireless devices (called “stations” in the 802.11 standard) connect to each other over a wireless network, a Basic Service Set (BSS) is formed. Because ad-hoc networks do not rely on any device other than the stations themselves, the wireless network they form is called an Independent Basic Service Set (IBSS). They are sometimes called peer-to-peer (wireless) networks.
Ad-hoc networks are limited in functionality because no central device is present to decide common rules (radio parameters, priority, range, what happens if the first station disappears, and so on). To organize the communication, most networks use a central device that defines common sets of parameters: the access point (AP, also called AP-station in the 802.11 standard). The AP organizes the BSS. Wireless devices send their signal to the AP, which relays the signal to the destination wireless station or the wired network. As such, the AP is a hybrid device, close to an Ethernet hub in concept: All stations share the same frequency, and only one station can send at any given time, forming a half-duplex network. An AP is more than a hub because it performs complex functions (generates or relays frames, for example). Like stations in an ad hoc network, an AP offers a BSS but not an IBSS, because the AP is a device dedicated to connecting stations. The area covered by the radio of this AP is called basic service area (BSA), orcell. Because the client stations connect to a central device, this type of network is said to use an infrastructure mode as opposed to an ad-hoc mode.
The wired section of the network that can be reached through the AP is called, from the perspective of the wireless side, the Distribution System (DS). When the distribution system links two APs, or two cells, the group is called an Extended Service Set (ESS). An ESS can be reached only through an AP BSS (not through an IBSS client also connected to the wired network). When a station moves, leaves the coverage area of the AP it was originally connected to, and gets to the BSA of another AP, the station is said to roam between cells. Neighboring cells are usually on different channels to avoid interferences. Wireless networks are designed to make neighboring cell detection and roaming seamless from the station standpoint. For the station to detect that the neighboring AP offers the same connection as the previous AP, wireless network administrators use names to identify wireless connections. Neighboring APs offering the same connection type and parameters use the same name, or service set identifier (SSID, which is a simple ASCII string providing a name to the connection). Neighboring APs offering the same connection use the same SSID, but each AP identifies itself by associating its radio MAC address to the SSID string. This associated MAC address is called the basic service set identifier (BSSID), and it enables stations to know which AP offers which SSID.
NOTE: Ad-hoc mode was described in the original 802.11 protocol and the 802.11b amendment. But ad hoc mode does not scale well, and later amendments (802.11g, 802.11a, 802.11i) do not describe this mode anymore. A consequence is that if you configure an ad-hoc network on a standard Wi-Fi certified laptop, your setup will limit your ad-hoc network to 2.4 GHz, 802.11 or 802.11 data rates (1, 2, 5.5, or 11 Mbps), with no authentication and no encryption, or with WEP security.
Wireless Topologies and Devices
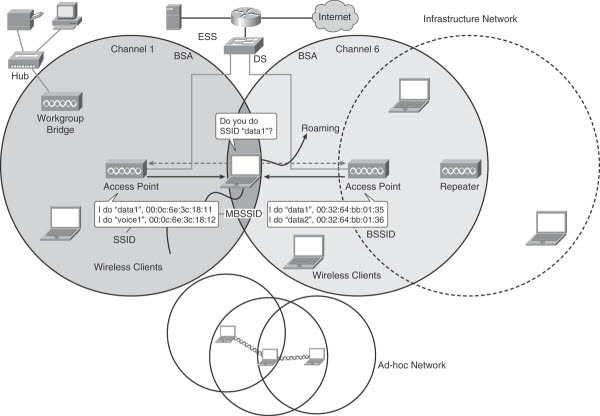
Some APs can offer only one SSID per radio. Other APs have a slot of MAC addresses available and can support several SSIDs per radio, using Multiple BSSIDs (MBSSID). MBSSIDs basically are virtual APs that still share the same physical device, which has a half-duplex radio. MBSSIDs are a way to differentiate the traffic reaching the AP, not a way to increase the capacity of the AP. Only one device can communicate at a time with an AP radio. MBSSID still enables you to create several SSIDs on the same AP radio, each SSID with a different name and individual authentication and encryption mechanisms. This way, stations on different SSIDs share the same RF space but are isolated from each other by different authentication and encryption mechanisms.
In a Cisco controller–based solution, APs attach to controllers. When the AP receives a client data frame, it decrypts any wireless encryption (WEP, TKIP, or AES-CCMP), then encapsulates the 802.11 frame into a CAPWAP packet and forwards this packet to the controller. To achieve the same isolation as on the wireless space, the controller can map each SSID to a different VLAN before releasing the forwarded traffic to the wired side of the network.
Reference from: https://www.ciscopress.com/articles/article.asp?p=1876001
More Wireless Topics:
Quiz Questions to Know Wireless LANs
Differences between WLANs, Wi-Fi and WiMax
802.11ac Wi-Fi vs. the 802.11n
Cisco 802.11ac Module for the Cisco 3600 Access Point
Cisco Enterprise-level Access Points Top Out at Nearly 400Mbps


