
To create a Lan to Lan VPN tunnel on an ASA firewall with IPv6 addressing, what needs to be done? LAN-to-LAN VPNs are typically used to transparently connect geographically disparate LANs over an untrusted medium (e.g. the public Internet). Here we’ll see what needs to be done in order to create a LAN-to-LAN VPN tunnel on an ASA firewall with IPv6 addressing.
First let’s begin with the fundamentals:
-IPv6 L2L VPN support was added in the latest version available of the ASA 8.3 track
-The ASA will be able to build a VPN site to site tunnel running IPv6 ONLY with another ASA.
Information taken from Cisco.com
For LAN-to-LAN connections using mixed IPv4 and IPv6 addressing, or all IPv6 addressing, the security appliance supports VPN tunnels if both peers are Cisco ASA 5500 series security appliances, and if both inside networks have matching addressing schemes (both IPv4 and both IPv6).
Specifically, the following topologies are supported when both peers are Cisco ASA 5500 series adaptive security appliances:
•The adaptive security appliances have IPv4 inside networks and the outside network is IPv6 (IPv4 addresses on the inside interfaces and IPv6 addresses on the outside interfaces).
•The adaptive security appliances have IPv6 inside networks and the outside network is IPv4 (IPv6 addresses on the inside interface and IPv4 addresses on the outside interfaces).
•The adaptive security appliances have IPv6 inside networks and the outside network is IPv6 (IPv6 addresses on the inside and outside interfaces)
If we want to run a VPN tunnel with a third-party unit or another Cisco router then we must go with the IPv4 address scheme only.
Now, let’s take a look at the Scenario:
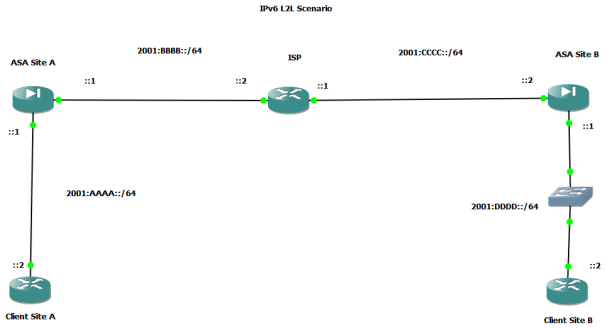
Our main goal here is to create a VPN tunnel using IPSec between Company A and Company B across an IPv6 network. IPv6 addressing and routing has been configured previously.
So now, let’s begin with the IPsec configuration
1) Specify as usual the phase 1 and phase 2 configuration
Site A:
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
crypto ikev1 enable outside
crypto ipsec ikev1 transform-set cisco esp-aes esp-sha-hmac
Site B:
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
crypto ikev1 enable outside
crypto ipsec ikev1 transform-set cisco esp-aes esp-sha-hmac
2) Now let’s move forward to the Interesting traffic configuration:
Site A Inside Subnet 2001:AAAA::/64
Site B Inside Subnet 2001:DDDD::/64
On Site A:
ipv6 access-list IPv6-Lab permit ip 2001:AAAA::/64 2001:DDDD::/64
On Site B:
ipv6 access-list VPN-Traffic permit ip 2001:dddd::/64 2001:aaaa::/64
So the Crypto ACL is the same thing, just that now we use Hex notation instead of Decimal notation
3) Crypto-Map Setup
Site A outside IPv6 address is 2001:BBBB::1
Site B outside IPv6 address is 2001:CCCC::2
So let’s go to the Firewall on Site A
Site A:
crypto map IPv6-L2L 1 match address IPv6-Lab
crypto map IPv6-L2L 1 set peer 2001:cccc::2
crypto map IPv6-L2L 1 set ikev1 transform-set cisco
crypto map IPv6-L2L interface outside
Site B:
crypto map IPv6-Lab 1 match address VPN-Traffic
crypto map IPv6-Lab 1 set peer 2001:bbbb::1
crypto map IPv6-Lab 1 set ikev1 transform-set cisco
crypto map IPv6-Lab interface outside
Now we will configure the final part. Is the Tunnel-group setup? …
Site A:
tunnel-group 2001:CCCC::2 type ipsec-l2l
tunnel-group 2001:CCCC::2 ipsec-attributes
ikev1 pre-shared-key cisco123
Site B:
tunnel-group 2001:BBBB::1 type ipsec-l2l
tunnel-group 2001:BBBB::1 ipsec-attributes
ikev1 pre-shared-key cisco123
Where is the NAT setup?
On IPv6 we do not have to use NAT in order to be routable over the internet so unless specific desing requirements we will not need to use NAT so we can forget about the NAT Exemption setup in our VPN cases.
Now let’s ping from Client A to Client B and see if the tunnel gets established:
SiteA-Client#ping 2001:DDDD::2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2001:DDDD::1, timeout is 2 seconds:
.!!!!
Now let’s check the tunnel
On Site A
SiteA(config)# sh crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 2001:cccc::2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
On Site B:
SiteB(config)# sh crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 2001:bbbb::1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
SiteB(config)#
Final notes:
-Configuration is the same, except for the fact that now we write down the IPs in Hex format ( That’s what IPv6 uses )
-There is no need for NAT Exemption anymore
-Debugs,Packet-tracers are the same ( For troubleshooting purposes ). If you plan to use CAPTURES, remember that in IPv6 you cannot use the match keyword, you must match the capture with an IPv6 ACL.
-Discussing about IPv6 ACL’s: Before 9.0(1) you must create a dedicated IPv6 access-list for IPv6 traffic as shown in this example but starting on 9.0(1) and higher versions now we can use the regular syntax for IPv6 access-list as well.
So we can use IPv6 and IPv4 on the same ACL, no need to create a dedicated IPv6 access-list. In fact the ASA will not allow you to do that.
Discussion from https://supportforums.cisco.com/docs/DOC-31021
More Related Topics:
Configuring LAN-to-LAN IPsec VPNs
https://www.cisco.com/en/US/docs/security/asa/asa83/configuration/guide/site2sit.html
More Related:
How to Enable IPv6 Support on a Cisco Catalyst 3560 Switch?
First Hop Redundancy Protocols in IPv6 HSRP + GLBP
What Hardware Vendor IPv6 Support


