
The new series of Cisco ASA devices (ASA 5500-X models which include 5512-X, 5515-X, 5525-X, 5545-X, 5555-X and 5585-X) have the capabilities to support Next Generation Firewall Security Services. They support these security services as cloud-based services (such as Cloud Web Security and Web Security Essentials) or as software based modules which do not need additional hardware (only a license to use the module).
Figure1. The ASA CX Architecture
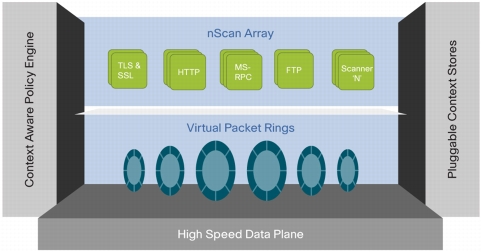
One of the prevalent security services modules is the ASA CX. This module has the following characteristics and compatibilities:
- It comes as a separate Hardware Module SSP on 5585-X firewall.
- It comes as a Software Module on ASA 5512-X through ASA 5555-X and is supported only on ASA version 9.1 and later.
- If you purchase a Cisco ASA 5512-X through ASA 5555-X with the ASA CX software module included, then you will get a device with a pre-installed SSD (Solid State Drive) which will have the ASA CX software ready to go.If you want to add the ASA CX to an existing ASA, or need to replace the SSD, you need to install the ASA CX boot software and partition the SSD with a special procedure.
The ASA CX security module receives traffic from the ASA hardware firewall and performs some advanced and extensive application inspection and control over this traffic. For example, with the ASA CX module, you can extract the full context of a traffic flow and enforce granular policies such as permitting access to Facebook but denying access to certain other functionalities of Facebook (such as playing Facebook games for example). Also, you can permit finance employees access to a sensitive enterprise database but denying the same to other employees. This Context-Aware security offered by ASA CX is based on identity of a user (who), the application or website that the user is trying to access (what), the origin of the access attempt (where), the time of the attempted access (when), and the properties of the device used for the access (how).
The ASA CX has its own GUI environment (different from the ASDM which manages the actual ASA firewall) and is managed with a Web Browser (for single installations) or using the Cisco Prime Security Manager (PRSM) which is a management tool for multiple ASA CX installations.
Taking advantage of the ASA CX is one of the differences between the older ASA5500 appliances and the new ASA5500-X series. ASA CX is supported only on the new 5500-X devices.
NOTE: If you don’t want to have these Next Generation Security services (which cost money to have) and you just want a plain firewall solution, then there are no major feature differences between the new ASA5500-X and the regular ASA5500 series (as far as core firewall services are concerned). However, you should keep in mind that the new 5500-X models are running on 64-bit processors and have much higher performance and throughput specs than the regular 5500 series.
—Resource from https://www.networkstraining.com
More…
Cisco ASA5510 Vs ASA5512-X or Cisco 5515-X
Cisco ASA 5500 Family, Key Component of the Cisco Secure Borderless Network
Simple Steps to Connect a Remote Office to Cisco ASA 5510
How to Configure Cisco ASA 5505 Firewall?
The Way to Activate Your Cisco ASA 5500
Cisco ASA 5520 Basic Configuration Guide
How to Configure Dual ISP on Cisco ASA 5505?
Site-to-Site IPSEC VPN between Two Cisco ASA 5520
More Info and Examples of Cisco ASA CX Security Module you can read related pages at Cisco.com
Cisco ASA CX Module Quick Start Guide
https://www.cisco.com/en/US/docs/security/asa/quick_start/cx/cx_qsg.html
Configuring the ASA CX Module
https://www.cisco.com/en/US/docs/security/asa/asa90/configuration/guide/modules_cx.html
Cisco ASA CX Context-Aware Security
https://www.cisco.com/en/US/prod/collateral/vpndevc/ps6032/ps6094/ps6120/qa_c67-700607.pdf


