
Here’s a lab that might be helpful for those working towards the CCNA examination.
We have a simple topology consisting of three routers. R8 will simply be used as a host on our “internal” network and R7 will be used as our border router (the serial connection between R5 and R7 will represent our connection to the Internet):
The goal is to NAT any traffic originating on our internal network (R8) as it leaves the serial 0/0 interface on R7 on its way to the “Internet” (R5). Overloading (having multiple clients all NAT’d to the same IP address) is probably the most common implementation (especially for those of us who run NAT on a Cisco box at home!).
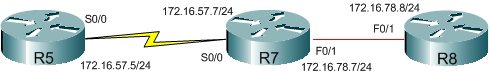
Let’s get basic connectivity working first:
R5# configure terminal
R5(config)# interface serial 0/0
R5(config-if)# ip address 172.16.57.5 255.255.255.0
R5(config-if)# no shutdown
R7# configure terminal
R7(config)# interface serial 0/0
R7(config-if)# ip address 172.16.57.7 255.255.255.0
R7(config-if)# no shutdown
R7(config-if)# interface fastethernet 0/1
R7(config-if)# ip address 172.16.78.7 255.255.255.0
R7(config-if)# no shutdown
R8# configure terminal
R8(config)# no ip routing
R8(config)# interface fastethernet 0/1
R8(config-if)# ip address 172.16.78.8 255.255.255.0
R8(config-if)# no shutdown
R8(config-if)# ip default-gateway 172.16.78.7
On R7, let’s verify we can ping both R5 and R8:
R7(config-if)# do ping 172.16.57.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.57.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms
R7(config-if)# do ping 172.16.78.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.78.8, timeout is 2 seconds:
..!!!
Success rate is 60 percent (3/5), round-trip min/avg/max = 1/2/4 ms
Alright, looks good. Now we can start with configuring NAT. First, let’s define our NAT inside and NAT outside interfaces (fastethernet 0/1 and serial 0/0, respectively):
R7(config-if)# interface fastethernet 0/1
R7(config-if)# ip nat inside
R7(config-if)# interface serial 0/0
R7(config-if)# ip nat outside
Next, we need to create an access-list to match the “internal” IP addresses (the ones we want to be NAT’d). In this case, our internal network is 172.168.78.0/24. Our ACL to match that network is simple:
R7(config-if)# ip access-list standard NAT
R7(config-std-nacl)# permit 172.16.78.0 0.0.0.255
Last, we’ll use the “ip nat …” command to actually instruct the router on what we want to NAT:
R7(config)# ip nat inside source list NAT interface serial 0/0 overload
This tells IOS that any packets coming in the “inside” interface (fastethernet 0/1) that are permitted by the named access-list “NAT” will have their “source” address translated to the IP address assigned to “interface serial 0/0″. In addition, NAT translations will be overloaded — that allows multiple devices inside to be translated to the same IP address.
To verify that NAT is working properly, let’s start a “debug ip icmp” on R5. Then, we’ll attempt to ping R5 from R8 and see what happens:
R5# debug ip icmp
ICMP packet debugging is on
R8(config)# do ping 172.16.57.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.57.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
We see that our pings were successful. What did R5 see?
R5# debug ip icmp
ICMP packet debugging is on
R5#
*Mar 1 19:07:25.603: ICMP: echo reply sent, src 172.16.57.5, dst 172.16.57.7
*Mar 1 19:07:25.611: ICMP: echo reply sent, src 172.16.57.5, dst 172.16.57.7
*Mar 1 19:07:25.615: ICMP: echo reply sent, src 172.16.57.5, dst 172.16.57.7
*Mar 1 19:07:25.619: ICMP: echo reply sent, src 172.16.57.5, dst 172.16.57.7
*Mar 1 19:07:25.623: ICMP: echo reply sent, src 172.16.57.5, dst 172.16.57.7
So R5 saw the echo requests and sent echo replies back, but notice the IP addresses. The source IP address of the echo replies is 172.16.57.5 (R5), but the destination IP address is 172.16.57.7 (R7). We can be sure that NAT is working, in part because R5 does not have a valid route to R8′s “real” IP address, 172.16.78.8:
R5# show ip route | begin Gateway
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 1 subnets
C 172.16.57.0 is directly connected, Serial0/0
R5# ping 172.16.78.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.78.8, timeout is 2 seconds:
…..
Success rate is 0 percent (0/5)
Be sure to check out the NAT translation table on R7, which should show a valid translation for the ICMP traffic that originated at R8:
R7(config)# do show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 172.16.57.7:0 172.16.78.8:0 172.16.57.5:0 172.16.57.5:0
Finally, we can use “debug ip nat” on R7 to see what’s happening there. Let’s turn that on, then ping R5 from R8 again:
R7# debug ip nat
IP NAT debugging is on
R8(config)# do ping 172.16.57.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.57.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
And what do we see on R7?
R7#
*Mar 1 19:15:13.695: NAT: s=172.16.78.8->172.16.57.7, d=172.16.57.5 [5]
*Mar 1 19:15:13.699: NAT*: s=172.16.57.5, d=172.16.57.7->172.16.78.8 [5]
*Mar 1 19:15:13.703: NAT*: s=172.16.78.8->172.16.57.7, d=172.16.57.5 [6]
*Mar 1 19:15:13.707: NAT*: s=172.16.57.5, d=172.16.57.7->172.16.78.8 [6]
*Mar 1 19:15:13.707: NAT*: s=172.16.78.8->172.16.57.7, d=172.16.57.5 [7]
*Mar 1 19:15:13.711: NAT*: s=172.16.57.5, d=172.16.57.7->172.16.78.8 [7]
*Mar 1 19:15:13.715: NAT*: s=172.16.78.8->172.16.57.7, d=172.16.57.5 [8]
*Mar 1 19:15:13.715: NAT*: s=172.16.57.5, d=172.16.57.7->172.16.78.8 [8]
*Mar 1 19:15:13.719: NAT*: s=172.16.78.8->172.16.57.7, d=172.16.57.5 [9]
R7#
*Mar 1 19:15:13.723: NAT*: s=172.16.57.5, d=172.16.57.7->172.16.78.8 [9]
R7#
We can see that the source IP address 172.16.78.8 (R8) is being translated to 172.16.57.7 (R7′s serial 0/0 interface). Success!
— Reference from evilrouters.net
More Related Networking Tips:
How to Configure Static NAT for Inbound Connections?


