
Do you know why does our network need routers, switches or firewalls? How many network equipment can deploy a useful network? In this post, we will discuss the development of network hardware. Enjoy it!
First, we share you an infographic about this topic:

Brought to you by Router-switch.com
Do you wish to publish this infographic on your website?
Copy below code and paste it into your web page editor:
<a href=”https://www.router-switch.com/faq/network-hardware-development.html”><img height=”5500″ width=”856″ src=” https://www.router-switch.com/media/upload/the-development-of-network-hardware.jpg” title=”Development Of The Network Hardware” alt=” Development Of The Network Hardware ” border=”0″ /></a><br/><br/> Brought to you by <a href=” https://www.router-switch.com/ “>Router-switch.com</a>
If you are tired to read so much content, you can view this video:
Then, let’s discuss these devices one by one.
How to Connect the PCs?
Before we invent the network, those personal computers work by themselves. There are not network cards, network cable or protocol stack. We mainly use floppy disk, CDs and other things to transfer data.
The Network Cable comes!
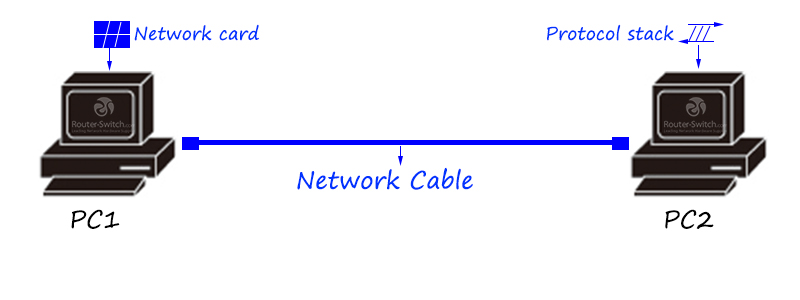
The minimum network unit consists of the network cable, network card and protocol stack. The network cable plays the role of physical medium, to carry bit stream/electric signal.
The network card will transform the data. For example, it transforms the data of computer storage to the bit stream/electric stream of the network cable.
The protocol stack, as a communication language, implements data analysis, address addressing, and flow control in the communication process.
What can we do if the network cable is not long enough?
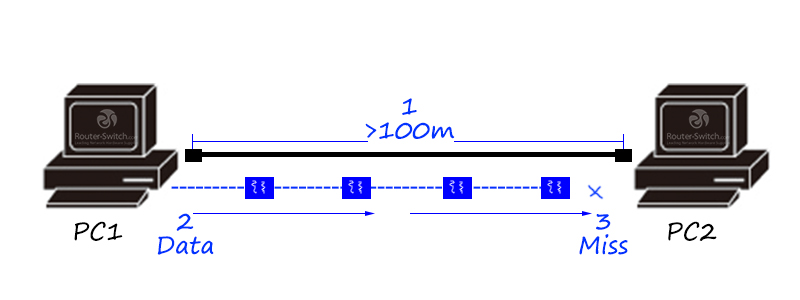
If the distance between terminals is too far, once the upper limit of the physical transmission distance of the network cable is exceeded, data will begin to be lost.
Here comes the repeater!
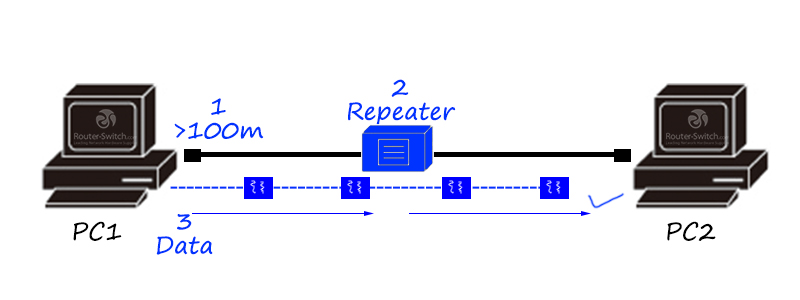
A repeater is a physical layer product that can relay and amplify information to achieve long-distance transmission of equipment.
What should I do if there are not enough repeater ports?
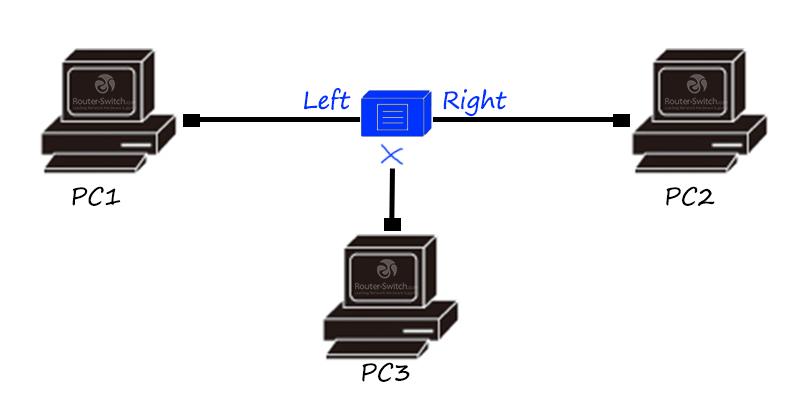
Repeaters generally only have two interfaces, which means that if there are more than three terminal hosts in the network, direct data communication between multiple hosts cannot be realized.
The hub is coming!
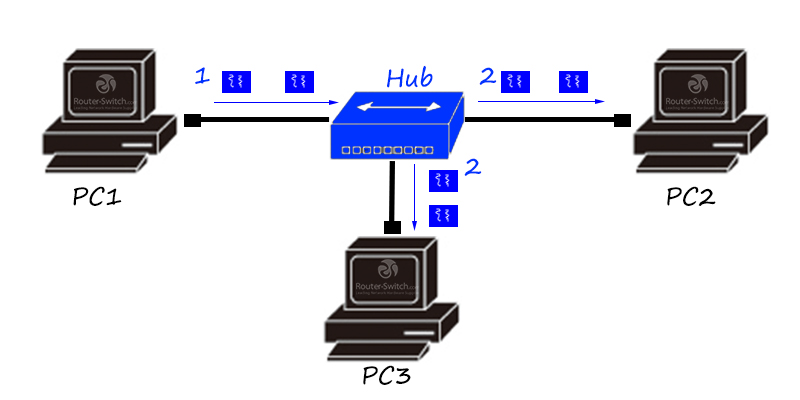
The hub is a multi-interface repeater, which is also a physical layer product. It can relay and amplify information. The data received from any interface will be flooded to all other interfaces.
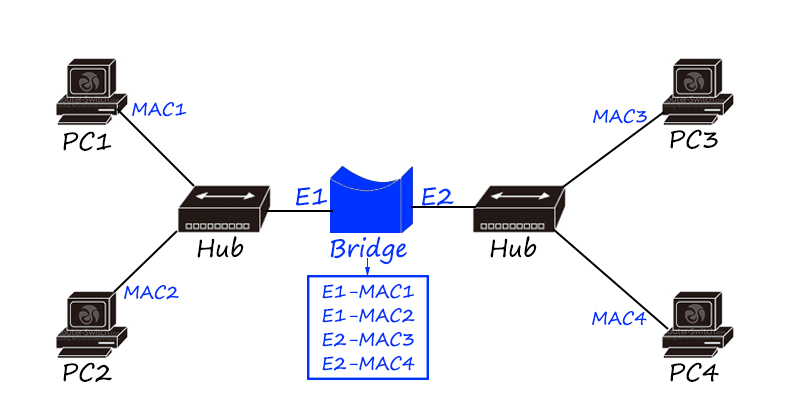
What should I do if I am afraid of harassment? The bridge is here!
What if it is not fast enough? The switch is here!
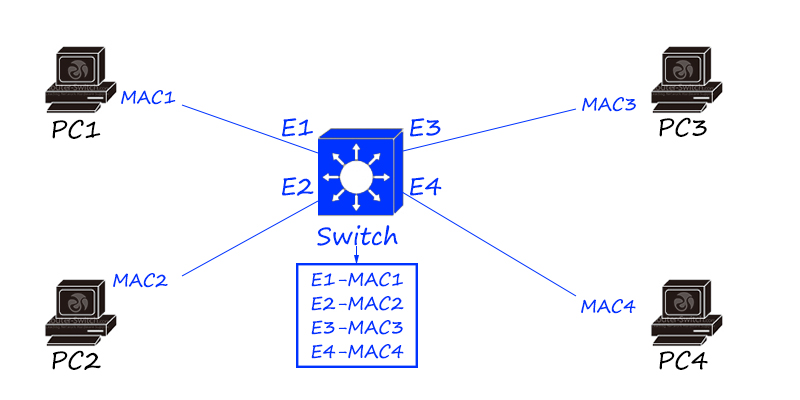
The switch is a link layer product that can record the MAC address of the terminal host and generate a MAC table (also called a CAM table). The MAC table is equivalent to a “map”. The switch forwards the data flow between hosts according to the MAC table.
Switches are extended and upgraded on the basis of network bridges. Compared with network bridges, they have several advantages:
- The number of interfaces is more dense (each host is in an independent collision domain, and bandwidth utilization is greatly improved)
- Use dedicated ASIC hardware chip for high-speed forwarding
- VLAN isolation (not only can isolate the conflict domain, but also isolate the broadcast domain through VLAN)
The switch is a local area network product, which is generally used in the local network and cannot realize remote WAN communication.
What if it is not far enough? The router is here!
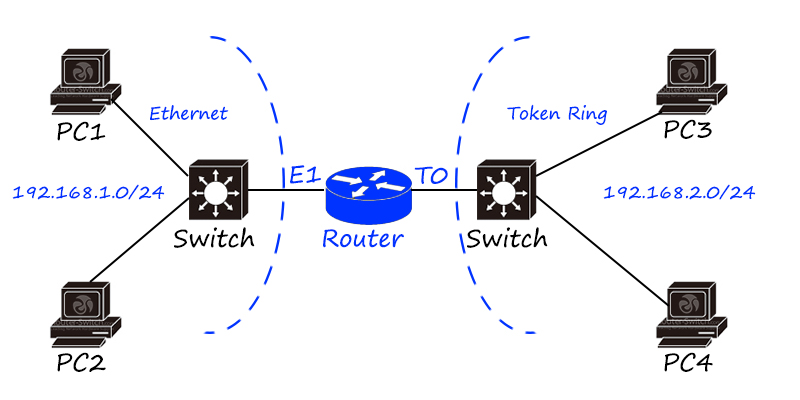
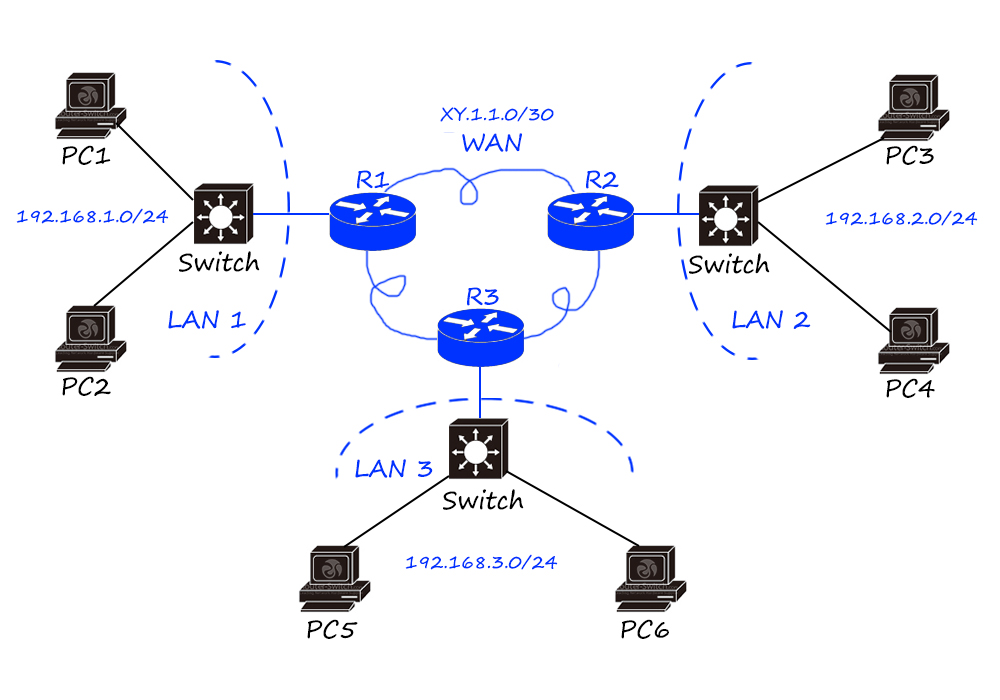
Router is a kind of network layer product, based on IP addressing, using routing table to realize data forwarding.
Routers are mainly used to connect different LANs to achieve broadcast domain isolation, and can also be used for remote communication, such as WAN connections.
The birth of routers is the main reason for the Internet explosion, and the cross-medium and cross-geographic network integration has become a reality.
The logical addressing mechanism such as IP protocol is the key to realize the connection of different types of LANs. As long as the hosts of different LANs have logical addresses (IP addresses) and reasonable logical address planning (network segment planning), they can communicate; routers are implementing LANs When communicating between them, “media flipping” and “route forwarding” will be performed.
The world’s first router was created by Leonard Bossack and Santi Lerner of Stanford University, a teacher couple, for Stanford University Campus Network (SUNet), and Cisco, the leader in the global network industry It was founded by this couple.
What should I do if the wiring is too troublesome? The wireless access point is here!
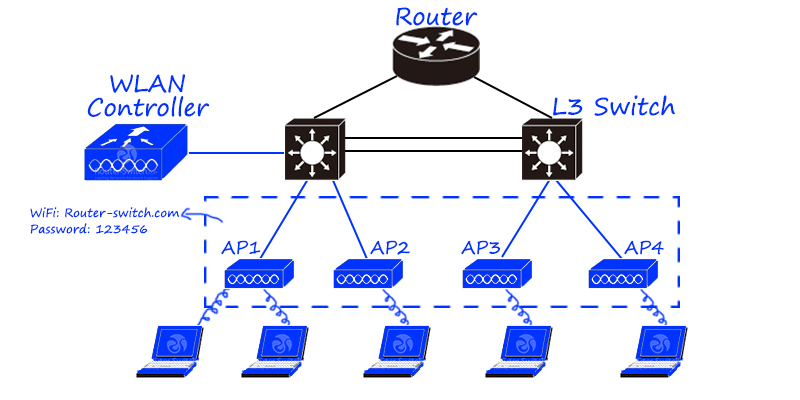
Wireless Ap (Access point) can be regarded as a switch/router with wireless function. With the trend of wireless cities and mobile office, the proportion of wireless products in the network is increasing.
According to different deployment methods, it can be divided into fat Ap and thin access point solutions. In the fat Ap scheme, the wireless Ap has an independent operating system, which can independently debug all configurations of the wireless hotspot, similar to the home Tp-link product. In the thin Ap scheme, the wireless Ap only has the function of wireless signal transmission, and all command debugging is concentrated on the AC/wireless controller in the background. Small wireless networks (home, small businesses) can be solved with fat APs, and large wireless networks (wireless cities, wireless campus networks) need to be solved with thin APs (AC + Ap).
What if it is not safe enough? The firewall is here.
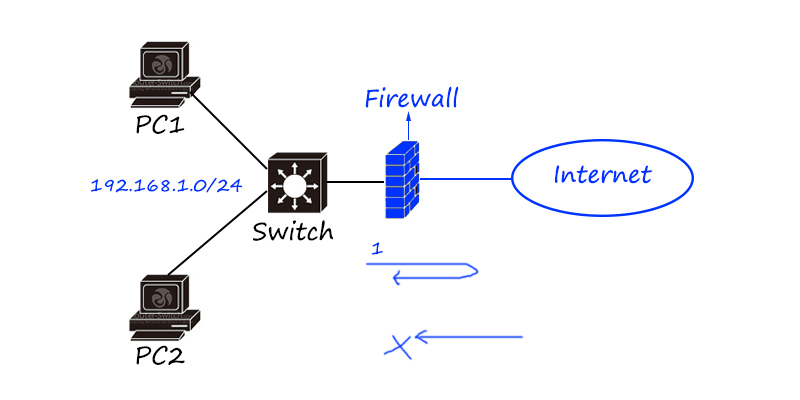
A firewall is a network security product used to restrict network security access. It is generally used at the edge of the Internet to prevent external hacker attacks.
According to the technical characteristics of the firewall, it can be divided into packet filtering, application proxy, and state detection firewall; according to the product form, it can be divided into software and hardware firewall.
Firewalls can be regarded as routers with security functions. Early firewalls added access control functions on the basis of routers, so many functions of firewalls can be seen on routers, such as routing protocols, access control lists, address flipping technology, etc.
Is there a firewall without a router? The router at the network border can be directly replaced as a firewall, but the firewall and the router can exist in the network at the same time. For example, the firewall can be placed before or after the router. In this case, the router focuses on address flipping and routing strategy, and the firewall focuses on security isolation, etc.
On the basis of firewalls, security products such as Web firewalls, security gateways, and intrusion detection/intrusion prevention have been extended.
What to do if the network is congested? Flow control is here!
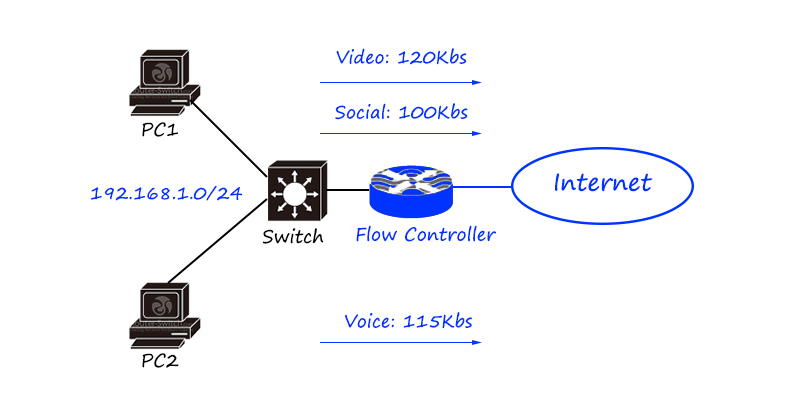
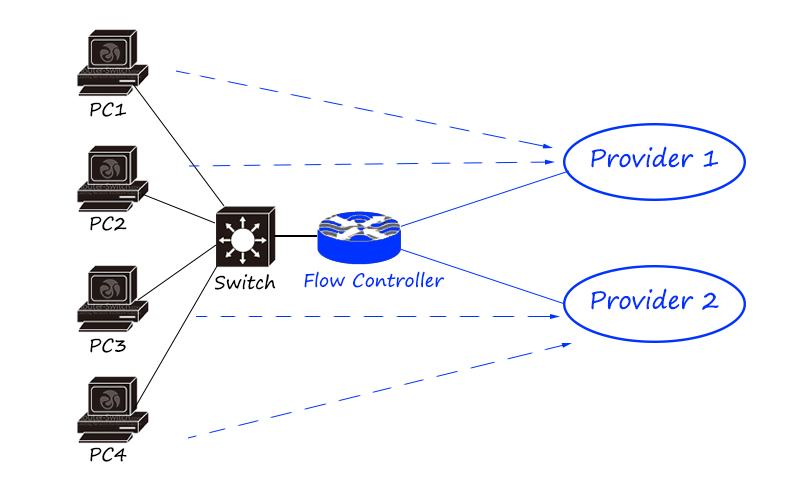
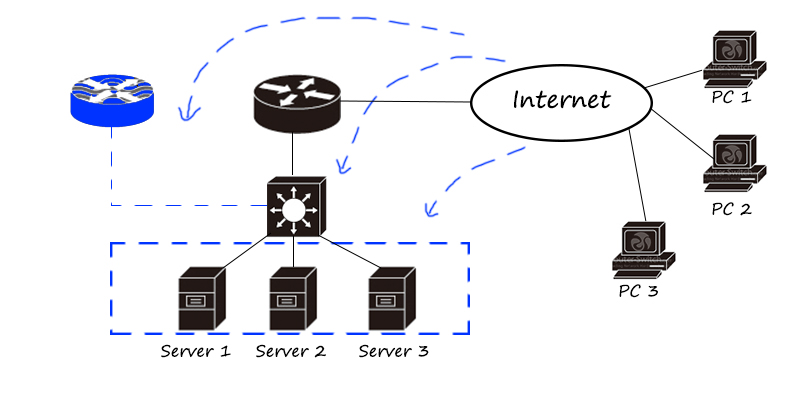
The flow control products in the network are mainly divided into online behavior management, load balancer/application delivery, link optimization, etc.
Behavior management products mainly focus on fine-grained differentiation and control of traffic. Two load balancing/application delivery focuses on load balancing of traffic (differentiated according to traffic characteristics, applications, addresses, etc., and then distributed to different links and servers); link optimization It is mainly used on the boundary of low-speed links such as wide area networks to maximize the use of links.
The flow control product is a seven-layer product that pays more attention to flow and application characteristics.
The question is, how many devices does a network need?
The Home SOHO network:
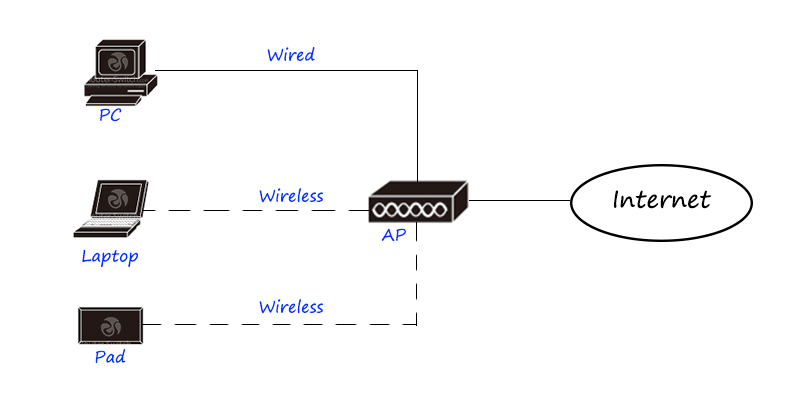
This is a typical home network, which provides WiFi hotspot access through a wireless router and provides a router to connect to the external network.
The Small business network:
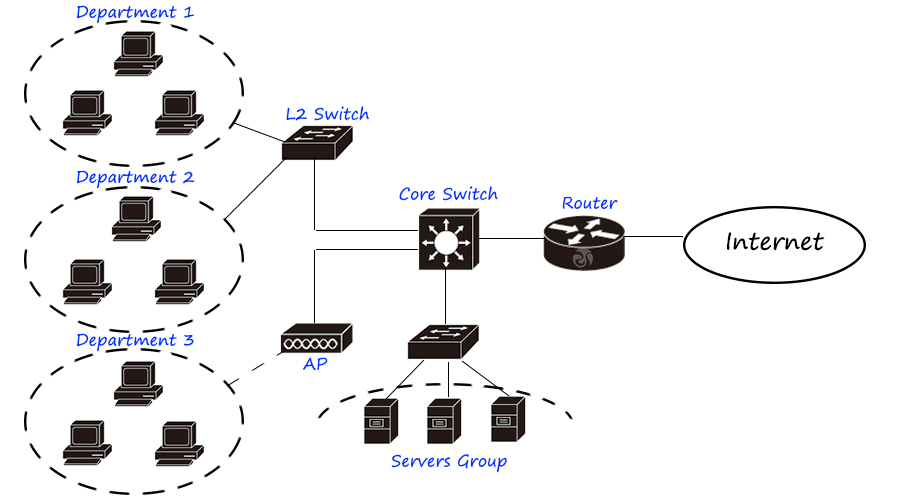
Small business network, using two-tier plus purchase, single-core topology, requires routers, switches, and servers.
The Campus network:
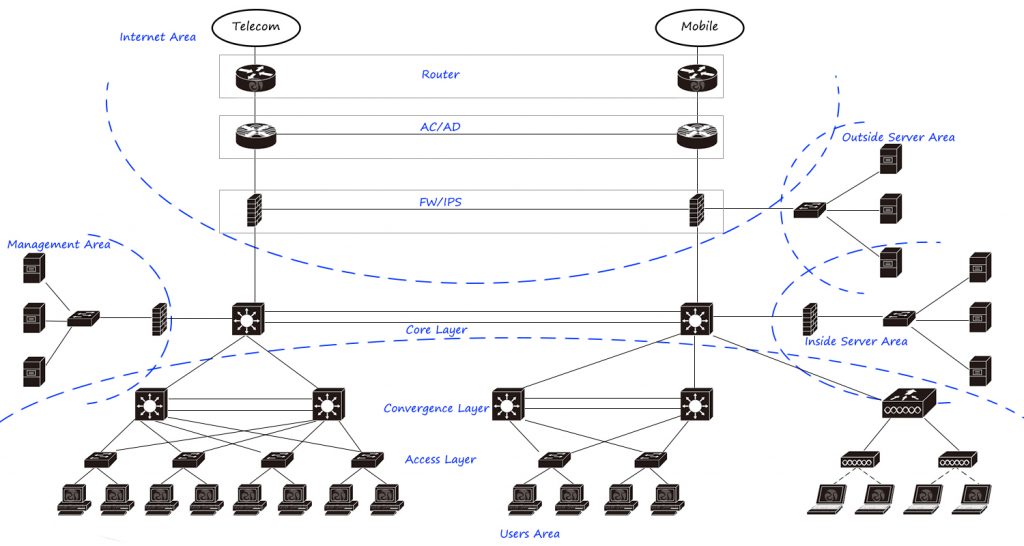
The most common campus network architecture, such as large and medium-sized enterprise networks/campus networks, uses a three-layer architecture of access convergence core and a dual-core network. According to network requirements, it is divided into user area, internal service area, external service area, management area, Internet area, etc., which are connected and isolated through core switches and firewalls. The Internet uses multi-outlet connections, dial-up and NAT through routers, load balancing/Internet behavior management through flow control products, and security isolation through firewalls.
The Data Center Network:
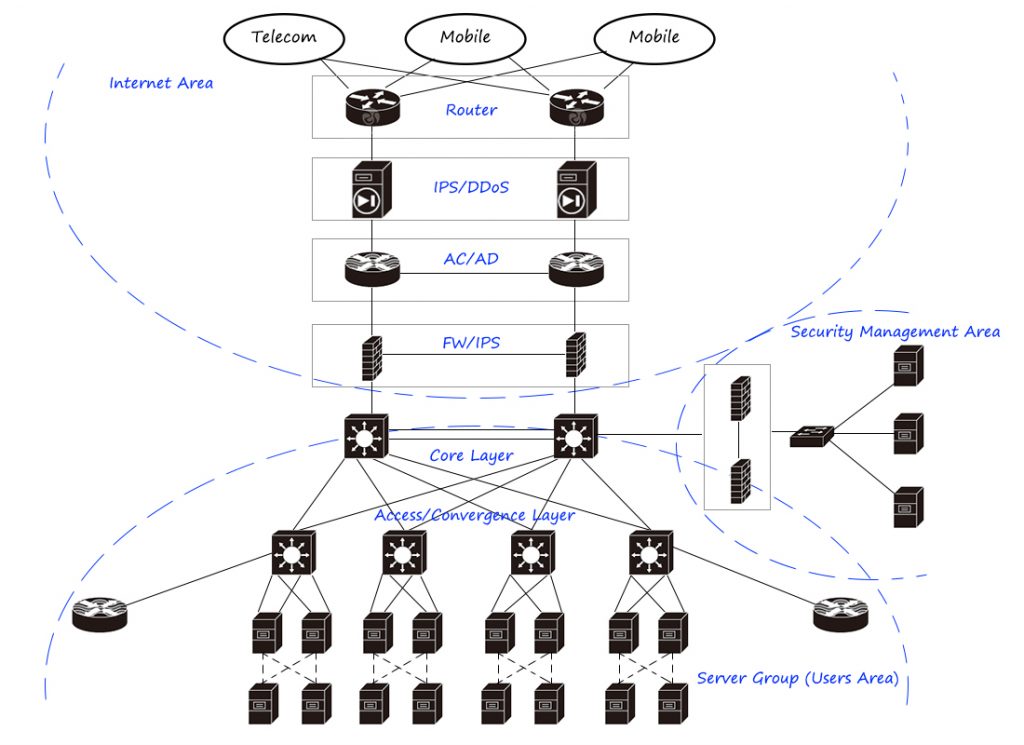
This is a typical large second-tier data center network/IDC design, which is mainly divided into tenant area (service cluster), Internet area, and security management area. Among them, the tenant area adopts equipment virtualization and link virtualization technologies to improve equipment processing capacity and link carrying capacity, and place load balancers in the server area to distribute traffic to fixed servers in a reasonable and effective manner. The Internet egress area uses routers to perform BGP and address reversal, uses IPS/anti-DDoS equipment to place large traffic flooding attacks, uses flow control to perform egress load, and uses firewalls for security isolation. The security management area is safely accessed through the firewall, and the entire network is managed through audit, log, intrusion detection, network management and other products.
There are many brands of network hardware, such as Cisco, Huawei, HPE, Dell, Juniper, Fortinet and so on. We can choose the right one for our needs.
If you have other questions, welcome to leave your comments.
Related Topics:
A Brief History of the Internet
Switch Setting: How to Build Intercommunication between Two Switches?


