We shared some topics about the DHCP before, such as the Five Things You Should Know About DHCP Snooping, How to Configure DHCP Snooping, How to Configure DHCP Snooping in a Cisco Catalyst Switch, DHCP Option 150 & DHCP Option 66, etc.
In this article we will continue to share someone’s experiences about the DHCP Snooping and Its Configuration.
What’s DHCP? How DHCP Works? What are the DHCP Snooping and DHCP Snooping Configuration? Now, let’s read the article below written by Mason Harris (CCIE No. 5916, a technical solutions architect for Cisco focusing on data center security architectures, with Cisco’s 20 largest customers.)
DHCP, it is a fundamental law of networking that hosts require addressing in order to communicate. In the early days of networking, devices were often assigned static addresses, since these resources rarely moved. But static addressing of hosts doesn’t scale. It’s hard to imagine that you have to manage your smartphone IP address every time you leave home. So, dynamic address configuration has become the de facto standard for the majority of networks around the world. Coffee shops, hotels, and your corporate network all utilize the Dynamic Host Configuration Protocol (DHCP) to make life a little easier for the myriad iPads, smartphones, and other computing devices that require access to your organization’s network and to the Internet.
DHCP snooping is a Layer 2 switch feature that mitigates the security risks posed by denial-of-service from rogue DHCP servers, which disrupt networks as they compete with legitimate DHCP servers that configure hosts on the network for communication.
In my experience, rogue DHCP servers are enabled most often by accident. For example: Wanting to extend wireless services into his workspace, a user plugs in an off-the-shelf wireless router that has DHCP enabled by default. Unbeknownst to the user, his new toy provides rogue addresses to unsuspecting hosts, creating reachability issues on the network.
Meanwhile, attackers take advantage of the open nature of DHCP to insert themselves between the host and the resource it’s trying to access, typically the Internet. This breach leads to man-in-the-middle exploits, in which unsuspecting users’ privacy and passwords could be compromised.
To help explain the challenges of dealing with rogue DHCP servers, let’s take a look at how DHCP works.
How DHCP Works
DHCP works on the simple premise that a client broadcasts a message (DHCPDISCOVER) to all hosts on the network, asking whether any DHCP servers are present. The originating client uses a unique identifier in the message—its Media Access Control (MAC) address—as a sort of return address.
If a DHCP server is listening and available, it responds in kind to the client, with a message (DHCPOFFER) stating the terms of the address lease. (If the network has multiple DHCP servers, the client typically responds to the first offer it receives.)
When the client accepts a lease offer, it responds with a request (DHCPREQUEST), which is followed by the DHCP server’s acknowledgment (DHCPACK). At this point, the client is configured and able to communicate on the IP network.
This simplicity has helped to make DHCP the underlying protocol in the vast majority of networks around the world today. (For additional technical details on DHCP, see Wikipedia’s DHCP page.)
Understanding DHCP Snooping
Cisco was the first vendor to release DHCP snooping as a feature in its network switches, designed to mitigate issues with rogue DHCP servers. Other vendors have since created similar features in their operating systems.
DHCP snooping is built on the concept of using one or more trusted ports that have been identified as having legitimate DHCP servers attached. As clients communicate on the network, the switch builds a “bindings table”—a database that lists the client MAC address, DHCP-assigned address, switchport, VLAN, and remaining DHCP lease time. The network switch then filters any DHCP server messages from untrusted ports in order to protect the integrity of legitimate DHCP servers and their operation.
NOTE: Best Practice: The bindings table is stored locally in memory but can be exported off-box via TFTP/FTP or RCP. Exporting this information is considered a best practice in case the Cisco switch unexpectedly reboots and loses all the data.
TIP: It’s important to note that Cisco’s implementation of DHCP snooping also drops frames in which the source MAC doesn’t match the embedded hardware address of the network interface card. This practice is fairly common in data centers today, where much communication depends on a specific MAC address.
DHCP Snooping Configuration
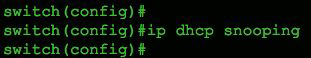
To begin enabling DHCP snooping, use the global command ip dhcp snooping as shown in the following figure
Global enablement of DHCP snooping on a Cisco switch
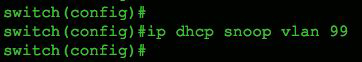
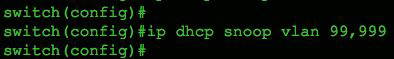
Next, configure the VLANs you want to protect, using the command ip dhcp snooping vlan 99. In the Figure below, we’re monitoring only VLAN 99, but we could easily include a range or sequence of VLANs, as shown in Figure” Multiple VLAN example”.
Single VLAN example
Multiple VLAN example
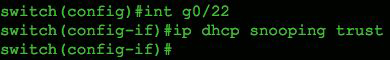
Finally, we need to tell the switch the port to which our trusted DHCP server is directly connected, as shown in the following Figure.
Trusted port configuration for a legitimate DHCP server
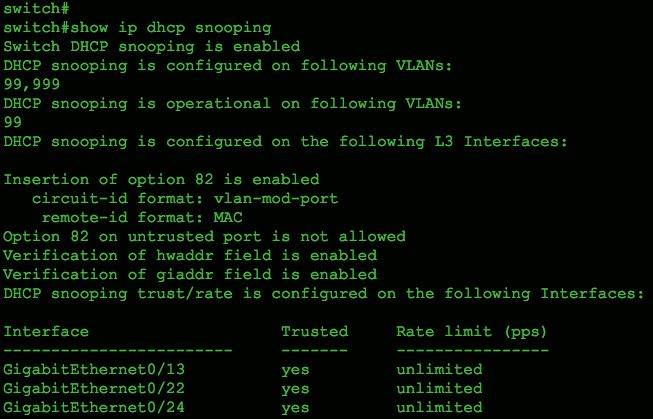
That’s it for a basic configuration on a Cisco switch. To verify proper operation, use the IOS command show ip dhcp snooping as shown in “Verification of proper DHCP snooping configuration”.
Notice that DHCP snooping is configured for both VLAN 99 and 999, but only operational on VLAN 99, as shown in the output.
Verification of proper DHCP snooping configuration
More advanced configurations allow for exporting the DHCP bindings database and rate-limiting DHCP server responses, as well as manipulating which hardware addresses are used for verification.
Understanding DHCP Option 82
In the early days of networking, networks tended to be “flat,” meaning that they had very few broadcast domains. In those days, DHCP servers could serve a large number of clients, because more hosts existed in larger broadcast domains. The downside to this scenario is that larger broadcast domains become very inefficient as they scale to larger sizes, due to the broadcast nature of Ethernet.
Network switches solved this issue by segmenting the networks into smaller chunks called virtual local area networks (VLANs). However, DHCP servers were still required in each VLAN to address hosts dynamically. This model clearly doesn’t scale (the number of DHCP servers would equal the number of VLANs), until the concept of relaying DHCP responses through Layer 3 devices was first implemented in RFC 3046. This design allowed hosts on remote VLANs to receive addresses from a DHCP server that was outside their subnet.
DHCP Option 82 allows DHCP relay-agent information to be inserted so that policies can be applied to remote hosts in accordance with the network addressing schema. Some vendors use these fields to implement their own extensions, and problems could arise if DHCP snooping is checking for specific values. Accordingly, Cisco devices can cause problems if these Option 82 fields don’t match. To makes matters even more complicated, the behavior of whatever is inserted in these fields may change from one software release to another!
Understanding how Option 82 extensions are used will aid in troubleshooting scenarios where hosts are not being addressed properly. For more information, see the Cisco article “Understanding and Troubleshooting DHCP in Catalyst Switch or Enterprise Networks.”
DHCP Snooping Operational Practices
When DHCP snooping detects a violation, the offending packet is dropped and an event is generated that contains the text DHCP_SNOOPING in the log message. Violations could occur from MAC address mismatches or attempts to provide DHCP services on untrusted ports.
Typically DHCP snooping is enabled on switches that contain access ports. A best practice is to also enable rate-limiting of DHCP requests on the untrusted ports. This IOS command is enabled at a port level and protects the DHCP server from excessive amounts of addressing requests. It’s enabled using this command:
ip dhcp snooping limit rate <1-4294967294>
where the variable number is expressed in packets per second.
What are the Mason Harris’ Final Thoughts on DHCP Snooping?
“I’d encourage anyone interested in deploying DHCP snooping in a production environment to test it in the lab first, to ensure a complete understanding of how the feature is intended to work. In my experience, most network engineers are familiar with the general concepts of DHCP, but a far smaller number understand the details, especially when it comes to proprietary vendor extensions and how they’re used.”
For more information on the DHCP protocol and its proper behavior, see the Internet Engineering Task Force (IETF) Request for Comments (RFC) 2131. RFCs detail the workings of a specific protocol or technology, and they’re a great place to start when you need to understand how something is intended to work in practice.
Original article from https://www.ciscopress.com/articles/article.asp?p=2474170
More Related…
Five Things You Should Know About DHCP Snooping
How to Configure DHCP Snooping
How to Configure DHCP Snooping in a Cisco Catalyst Switch
DHCP Option 150 & DHCP Option 66
DHCP Relay on the Nexus7000/NXOS Vs. IP Helper on the 6500/IoS