
At a high level, What the ASA failover is? It is simple to describe the Cisco ASA failover: Two devices are connected to the network as they normally would be, and they are connected to each other to communicate failover information. When the ASA detects a device or interface failure, a failover occurs.
What exactly happens when a failover occurs depends on the mode of failover being used?
There are two different failover modes that are supported on the ASA platform: active/passive and active/active. When using the active/passive failover mode, one ASA is considered the Active partner and is used to process and forward all traffic, while the passive partner monitors the active partner for a failure to occur.
If this should happen, the passive partner will take over the forwarding duties from the active partner. When using the active/active failover mode, both ASAs can forward traffic at the same time. When using this failover mode, failover does not occur on a system-to-system basis; it occurs on a failover group–to–failover group basis.
One of the failover groups is typically assigned to the primary failover unit, and the other is typically assigned to the secondary unit. For active/active failover mode to be supported, the ASA model must support multiple context modes. Each context is configured into one of two failover groups.
Failover Types
Within these two different failover modes, there are also two different failover types: stateless and stateful. When using stateless failover, if a failover should need to occur, all active connections will be dropped and will have to be reestablished to continue communications.
When using stateful failover, connection state information is exchanged between the failover partners (or groups). If a failover should need to occur, the active connections (that are supported) can be seamlessly transferred and will not need to be reestablished.
ASA Failover Addresses
When ASA failover is configured, a primary and secondary IP address are configured. When a failover occurs, the secondary partner will take over both the primary IP addressand the primary MAC address, while the former primary partner will take over the secondary IP address and the secondary MAC address.
Failover Requirements
There are a couple of hardware and software requirements that need to be met for failover configuration to be successful. These requirements are listed below:
Hardware:
- ASA failover partners must be the same model.
- ASA failover partners must have the same number and types of interfaces.
- ASA failover partners must have the same modules installed (if any are to be installed).
- ASA failover partners must have the same amount of RAM installed (it is also preferred if the Flash sizes are the same as well).
Software:
- Both ASA failover partners must be using the same firewall mode (routed or transparent).
- Both ASA failover partners must be using the same context mode (single or multiple).
- Both ASA failover partners must be using the same major and minor software version (there are exceptions during upgrade).
- Both ASA failover partners must use the same AnyConnect images.
Physical Failover Connectivity
When connecting the two different ASA failover partners, there are possibly two different failover specific links that need to be connected. How exactly they are connected depends on the specific configuration.
The first of these failover links is called the failover link; this link is used to determine the operating status of the paired device. There are two different ways to connect the failover link: using a switch or using a direct cable between the paired devices. When using a switch for this connectivity, ensure that it is configured to be on a separate VLAN from any other traffic. This link can use any unused ASA interface including physical, redundant, and EtherChannel.
The second of these failover links is called the stateful failover link. As is obvious from the name, this link is used only if the stateful failover mode is used. This link is used to pass per-connection state information between failover partners (or failover groups) and can include a large amount of data.
For the stateful failover link, there are three different ways that it can be configured: using a dedicated interface (either a direct cable between ASA ‘s or using an isolated VLAN through a switch), sharing the failover link, or sharing with a regular data interface.
For any ASA implementation in which the number of connections will be high, it is recommended that a dedicated interface be used. If the number of connections will be moderate, sharing the failover link is possible, but performance should be monitored to ensure that the stateful traffic is not taking over the link. The third option is to share a regular data interface. Generally, this is never recommended unless there is no other option.
One very important thing to note is that, by default, all information that goes over the failover link and stateful failover link is sent in clear text. This can be changed by either configuring the use of an IPSec tunnel or by configuring a failover key.
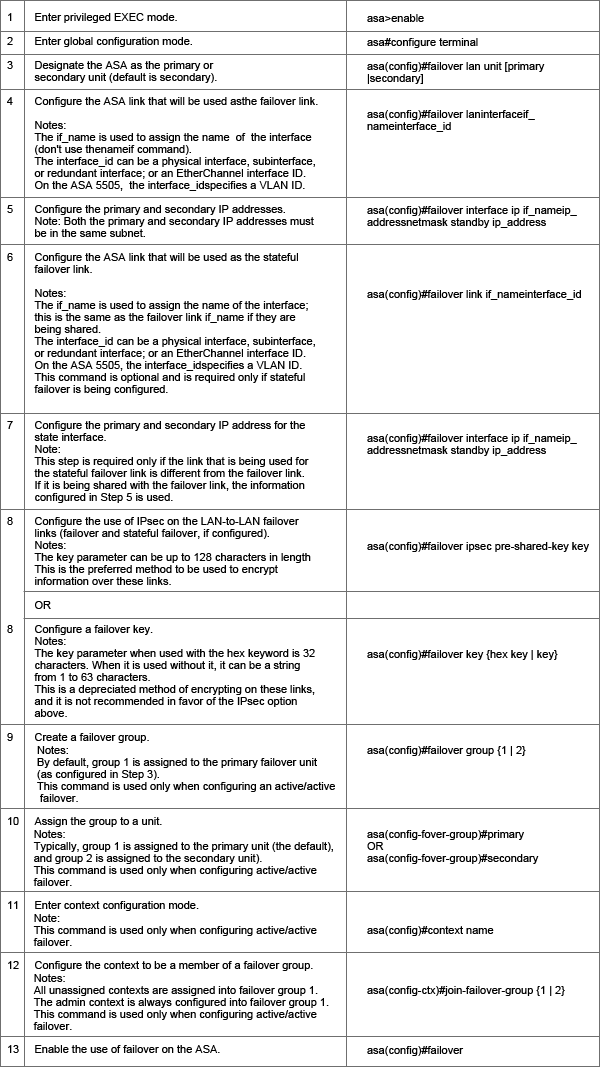
ASA Failover Configuration
When you configure Cisco ASA failover, there are several commands that are common between active/passive, active/active, and stateless/stateful. We will show the configuration commands in the same table with the appropriate notes noting command usage as follows.
Table: ASA Failover Configuration
What should be taken out of this article are the basic concepts of what is possible with ASA failover and how it can be used to improve the availability of the network it is protecting.The specific failover configuration that is used can vary quite a bit depending on the specific implementation. Because this article was intended to cover the basic failover options and configuration, some failover options were not covered, including interface monitoring configuration options, transparent firewall mode options, and the management of failover[md]just to name a few.
Reference article from https://www.ciscopress.com/
More Cisco ASA Reviews and Topics:
Cisco ASA IPS Module Configuration
WAYS to Help You Set Up Your Small, Medium and Large Networks
How to Configure New ASA 5510 in Transparent Mode?
Cisco Security Advisory: Multiple Vulnerabilities in Cisco ASA Software


