
In today’s network world, almost all applications tunnel themselves over HTTP, either due to their nature as web-based apps or the fact that they take advantage of port 80 being open through almost every firewall. The key to being able to identify malicious or non-desired traffic attempting to use HTTP as a “common carrier” is to inspect the packet at a deeper level than just port number.
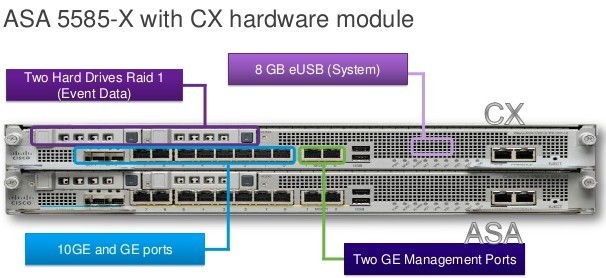
The Cisco ASA CX is a Security Services Processor (SSP) module that today runs on the ASA 5585-X model. It’s a beastly server-type device that has 12GB or 24GB or RAM, 600GB of RAID-1 disk space and 8GB of flash storage. The lower-end model can take up to 2Gbps throughput and the bigger brother can handle 5Gbps. It scans over 1000 applications and more than 75,000 “micro” applications to determine whether the user is listening to iTunes in the cloud or watching HD video on Youtube. The ASA CX also utilizes other products in the Cisco Secure-X portfolio to feed it information. The Cisco AnyConnect Secure VPN client allows the CX to identify traffic that isn’t HTTP-based, as right now the CX can only identify traffic via HTTP User Agent in the absence of AnyConnect. In addition, the Cisco Security Intelligence Operation (SIO) Manager can aggregate information from different points on the network to give the admins a much bigger picture of what is going on to prevent things such as zero-day attack outbreaks and malware infections.
One of the nice new features of the ASA CX that’s been pointed out by Greg Ferro is the user interface for the CX module. Rather than relying on the Java-based ADSM client or forcing users to learn yet another CLI convention, Cisco decided to include a copy of the Cisco Prime Security Manager on-box to manage the CX module. This is arguably the best way for Cisco to have created an easy way for customers to easily utilize the features of the new CX module. Instead, with the CX Prime Security Manager interface, Cisco has allowed us to take a UI and apply it to the new features in the firewall module. In addition, we can forego the use of the on-box Prime instance and instead register the CX to an existing Prime installation for a single point of management for all our security needs. We’re sure that the firewall itself still needs to use ASDM for configuration and that the Prime instance is only for the CX module but this is still a step in the right direction.

There are some downsides to the CX right now. That’s to be expected in any 1.0-type launch. Firstly, you need an ASA 5585-X to run the thing. That’s a pretty hefty firewall. It’s an expensive one too. It makes sense that Cisco will want to ensure that the product works well on the best box it has before trying to pare down the module to run effectively on the lower ASA-X series firewall. And we still doubt that Cisco will ever port this module to run on the plain ASA series. So if you want to do Next-Gen firewalling, you’re going to need to break out the forklift no matter what. In the 1.0 CX release, there’s also no support for IPS, non-web based application identification without AnyConnect, or SSH decryption (although it can do SSL/TLS decryption on the fly). It also doesn’t currently integrate with ISE for posture assessment and identity enforcement. That’s going to be critical in the future to allow full integration with the rest of Secure-X.
If you’d like to learn more at the new ASA CX, check out the pages on Cisco’s website. There’s also an excellent Youtube walkthrough:
Someone’s Take
“Cisco has needed a Next-Gen firewall for quite a while. When the flagship of your fleet looks like the Stargazer instead of the Enterprise-D, it’s time for a serious upgrade. I know that there have been some challenges in Cisco’s security division as of late, but I hope that they’ve been sorted out and the can start moving down the road. At the same time, I’ve got horrible memories of the last time Cisco tried to extend the Unified Threat Management (UTM) profile of the ASA with the Content Security and Control (CSC) module. That outsourced piece of lovely was a source of constant headache for the one or two customers that had it. On top of it all, everything inside was licensed from Trend Micro. That meant that you had to pay them a fee every year on top of the maintenance you were paying to Cisco! Hopefully by building the CX module with Cisco technologies such as Network-Based Application Recognition (NBAR) version 2, Cisco can avoid having the new shiny part of its family being panned by the real firewall people out there and languish year-to-year before finally being put out of its misery, much like the CSC module or Enterprise. I’m sure that’s why they decided to call the new module the CX and not the NX. No sense cursing it out of the gate.”
Original article you can read at: https://networkingnerd.net/
More Cisco Firewall Topics:
Migrating from Cisco ASA 5500 Series to ASA 5500-X Series
What is Cisco ASA CX Security Module?
Cisco ASA5510 Vs ASA5512-X or Cisco 5515-X
What Things to be Considered While Upgrading ASA 5500 Series?


