
How CAN you monitor your remote ASA over Ipsec Lan-to-Lan tunnel? Here in this article we will show the way to monitor your remote ASA over Ipsec Lan-to-Lan tunnel.
Scenario:
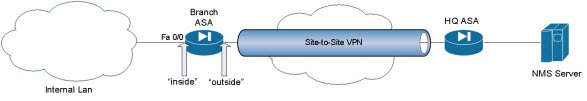
In our case we will try to use a common scenario, where you have HQ ASA and branch ASA which should be monitored/polled over VPN tunnel (which is in between). SNMP/NMS server will be behind the HQ ASA. In our test we will try to monitor/poll interface fastEthernet 0/0 on Branch ASA from SNMP/NMS Server.
NMS/SNMP server: 192.168.1.3/24
Branch ASA FastEthernet 0/0: 5.5.5.1/24
Topology:
Solution:
VPN configuration part:
On Branch ASA:
…
crypto ipsec ikev1 transform-set TRANS esp-3des esp-sha-hmac
…
crypto map MAP 10 match address ACL
crypto map MAP 10 set peer $peer ip address$
crypto map MAP 10 set ikev1 transform-set TRANS
crypto map MAP interface outside
crypto ikev1 enable outside
…
tunnel-group $peer ip address$ type ipsec-l2l
tunnel-group $peer ip address$ ipsec-attributes
ikev1 pre-shared-key cisco
…
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
…
In ACL for encryption you should have ip address/subnet of fastethernet interface 0/0 (or whatever)
# access-list ACL extended permit ip 5.5.5.0 255.255.255.0 192.168.1.0 255.255.255.0
On HQ ASA:
…
crypto ipsec ikev1 transform-set TRANS esp-3des esp-sha-hmac
…
crypto map MAP 10 match address ACL
crypto map MAP 10 set peer $peer ip address$
crypto map MAP 10 set ikev1 transform-set TRANS
crypto map MAP interface outside
crypto ikev1 enable outside
…
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
…
tunnel-group $peer ip address$ type ipsec-l2l
tunnel-group $peer ip address$ ipsec-attributes
ikev1 pre-shared-key cisco
In ACL for encryption should be defined ip address/subnet of NMS/SNMP server.
# access-list ACL extended permit ip 192.168.1.0 255.255.255.0 5.5.5.0 255.255.255.0
SNMP part:
On Branch ASA:
1. You need to configure SNMP server and define interface behind which server is located, and this is a tricky part, since you need to define “inside” interface in order to push snmp traffic over the tunnel:
# snmp-server host inside 192.168.1.3 community test version 2c
2. You need to configure your “inside” interface as “management-access”.
# management-access inside
Verification:
We’ve done verification with “snmpwalk” command from snmp server:
root@VM:~# snmpwalk -v 2c -c test 5.5.5.1
iso.3.6.1.2.1.1.1.0 = STRING: “Cisco Adaptive Security Appliance Version 8.4(2)”
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.9.1.227
iso.3.6.1.2.1.1.3.0 = Timeticks: (134200) 0:22:22.00
iso.3.6.1.2.1.1.4.0 = “”
iso.3.6.1.2.1.1.6.0 = “”
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
iso.3.6.1.2.1.2.1.0 = INTEGER: 8
iso.3.6.1.2.1.2.2.1.1.2 = INTEGER: 2
iso.3.6.1.2.1.2.2.1.1.3 = INTEGER: 3
iso.3.6.1.2.1.2.2.1.1.4 = INTEGER: 4
…
Reference links:
1. https://www.cisco.com/en/US/products/ps6120/products_tech_note09186a00807e0aca.shtml
2. https://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_tech_note09186a0080094a13.shtml
3. https://www.cisco.com/en/US/docs/security/pix/pix72/quick/guide/sitvpn_p.html
Reference from https://supportforums.cisco.com/docs/DOC-34759
More Related:
Secure SNMP in Cisco Switches and Routers


