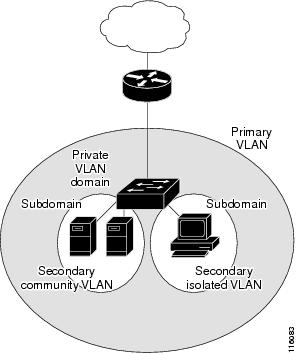
The private-VLAN feature addresses two problems that service providers face when using VLANs:
1. Scalability: The switch supports up to 1005 active VLANs. If a service provider assigns one VLAN per customer, this limits the numbers of customers that the service provider can support.
2. To enable IP routing, each VLAN is assigned a subnet address space or a block of addresses, which can waste the unused IP addresses and cause IP address management problems.
Tips: Using private VLANs addresses the scalability problem and provides IP address management benefits for service providers and Layer 2 security for customers.
Notes: Private VLANs partition a regular VLAN domain into subdomains and can have multiple VLAN pairs—one for each subdomain. A subdomain is represented by a primary VLAN and a secondary VLAN. All VLAN pairs in a private VLAN share the same primary VLAN. The secondary VLAN ID differentiates one subdomain from another.
There are two types of secondary VLANs:
Isolated VLANs—Ports within an isolated VLAN cannot communicate with each other at the Layer 2 level.
Community VLANs—Ports within a community VLAN can communicate with each other but cannot communicate with ports in other communities at the Layer 2 level.
Private VLANs provide Layer 2 isolation between ports within the same private VLAN.
Private-VLAN ports are access ports that are one of these types:
Isolated port: An isolated port is a host port that belongs to an isolated secondary VLAN. It has complete Layer 2 separation from other ports within the same private VLAN, except for the promiscuous ports. Private VLANs block all traffic to isolated ports except traffic from promiscuous ports. Traffic received from an isolated port is forwarded only to promiscuous ports.
Command: switchport mode private-vlan host
Community port: A community port is a host port that belongs to a community secondary VLAN. Community ports communicate with other ports in the same community VLAN and with promiscuous ports. These interfaces are isolated at Layer 2 from all other interfaces in other communities and from isolated ports within their private VLAN.
Command: switchport mode private-vlan host
Promiscuous port: A promiscuous port belongs to the primary VLAN and can communicate with all interfaces, including the community and isolated host ports that belong to the secondary VLANs associated with the primary VLAN.
Command: switchport mode private-vlan promiscuous
Tasks for Configuring Private VLANs
Step 1 Set VTP mode to transparent.
vtp mode transparent
Step 2 Create the primary and secondary VLANs and associate them
Switch(config)# vlan 20
Switch(config-vlan)# private-vlan primary
Switch(config-vlan)# exit
Switch(config)# vlan 501
Switch(config-vlan)# private-vlan isolated
Switch(config-vlan)# exit
Switch(config)# vlan 502
Switch(config-vlan)# private-vlan community
Switch(config-vlan)# exit
Switch(config)# vlan 20
Switch(config-vlan)# private-vlan association 501-502
Step 3 Configure interfaces to be isolated or community host ports, and assign VLAN membership to the host port
Switch(config)# interface fastethernet0/22
Switch(config-if)# switchport mode private-vlan host
Switch(config-if)# switchport private-vlan host-association 20 501
Step 4 Configure interfaces as promiscuous ports, and map the promiscuous ports to the primary-secondary VLAN pair
Switch# configure terminal
Switch(config)# interface fastethernet0/2
Switch(config-if)# switchport mode private-vlan promiscuous
Switch(config-if)# switchport private-vlan mapping 20 add 501-502
Switch(config-if)# end
Cisco Switches Support Private VLANs—Full Features(Community & Isolated VLAN):
1) Catalyst 6500/6000 – CatOS on Supervisor and Cisco IOS on MSFC 5.4(1) on Supervisor and 12.0(7)XE1 on MSFC
2) Catalyst 6500/6000 – Cisco IOS System software +12.1(8a)EX, 12.1(11b)E1
3) Catalyst 4500/4000 – CatOS + 6.2(1)
4) Catalyst 4500/4000 – Cisco IOS +12.1(8a)EW 12.2(20)EW(Community VLAN)
5) Catalyst 3560 + 12.2(20)SE – EMI
6) Catalyst 3750 + 12.2(20)SE – EMI
7) Catalyst 2948G/2980G + 6.2
Cisco Catalyst Switches Support PVLAN Edge (Protected Port)
1) Catalyst 3550 + 12.1(4)EA1
2) Catalyst 2950 + 12.0(5.2)WC1, 12.1(4)EA1
3) Catalyst 2900XL/3500XL + 12.0(5)XU (on 8MB switches only)
4) Catalyst 3560 + 12.1(19)EA1
5) Catalyst 3750 + 12.1(11)AX
6) Catalyst 3750 Metro + 12.1(14)AX
7) Catalyst 2940 + 12.1(13)AY
8) Catalyst 2955
9) Catalyst 2970
More Private VLANs Details and Tips:
Catalyst 3560 Software Configuration Guide-Configuring Private VLANs at Cisco.com (Detailed Document with Full Examples)
Cisco Fans Talk about: Private VLANs on a Cisco 3560G