How to configure Local Username Database in Cisco IOS? David Davis, the director of Infrastructure at Train Signal – the global leader in video training for IT Pros, wrote the article “Configuring Local Username Database in Cisco IOS”. In this article, we will take a step further in securing our Cisco router by using a local username / password database in the Cisco IOS. Thus, a user must know a username AND password to be granted access to the Cisco IOS. Let’s see how this is done.
Local Authentication
The most basic level of security you can configure on a Cisco IOS device is a password. When this is done, a password is assigned to allow access to the privileged/global configuration mode, and to protect initial entry to the user mode of the IOS.
However, the Cisco IOS can take this a step further, and have actual usernames and passwords assigned for access. By doing this, you have the real name of the person who is accessing the device. If you chose to do so, this username could be logged so that you know when that user logged into the router, and when they logged off.
The Cisco IOS can, of course, also support external authentication through services like Cisco ACS and RADIUS. In this example, we will create a basic local authentication database containing usernames and passwords, and then use that to login to the Cisco IOS device.
Creating the Database
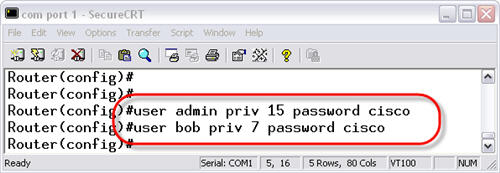
To create the user database, you use the username command. Let’s create 2 users with different privileges. The Admin user will have level 15 (Cisco administrator / super-user access). The user Bob will have level 7 access (moderate user access). Here is how it is done:
username admin priv 15 password cisco username bob priv 7 password cisco
Once these users are created, you need to enable the login on the lines to use the local database instead of just the line password, or no password at all.
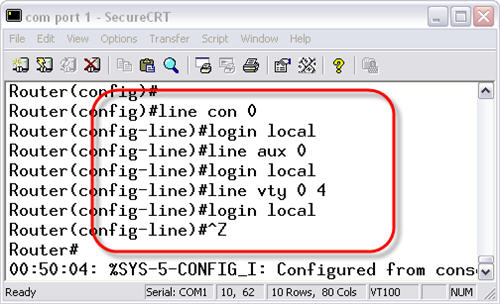
Enabling Lines to use the Local Authentication Database
To tell each line to use these new user logins, you must go to each line and perform the login local command. This is different than just the login command, by itself. The login command enables password checking. By using only the login command, you are only enabling password checking for the line password, configured on that line. By using login local, you are telling the device to use the locally configured accounts in the username database. Here is how you configure it:
Let’s test it out!
Testing Local Login Authentication
To test our new usernames and the local line authentication we configured, log out of the router. Log back in and you should be prompted with a Username: prompt.
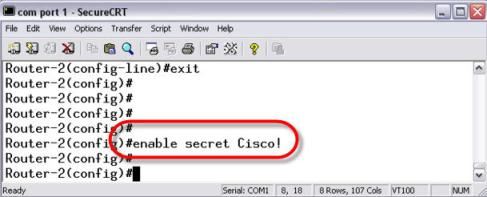
The enable secret command does encrypt the password with a strong encryption mechanism and it also sets a password to enter enable mode. Here is how you configure an enable secret password:
Testing Password Configuration
To test our new password configuration from the console port, exit out of all IOS modes. Once logged off, press enter to log back in.
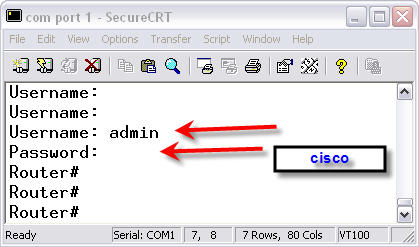
Here is an example where I logged in with the admin account we created. I used the password “cisco”. Notice how I was immediately brought to the Router# prompt, without having to type an enable password. This is because I used the command privilege 15 on the username when I created it. That level of privilege also gives me full administrative access to the router.
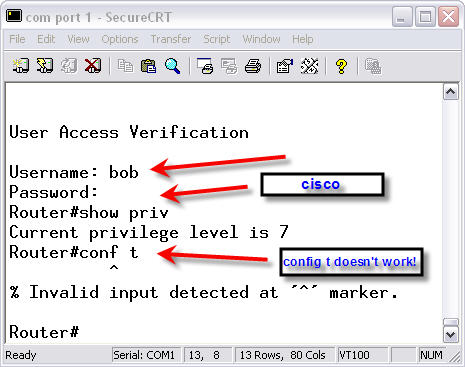
After logging off, I logged back in as the bob user. Here is an example:
Notice in this example that this user was put into privilege mode 7, but this mode still didn’t allow them to access the global configuration mode. You can get very advanced when it comes to configuring privilege levels and commands in privilege levels.
At this point, we have successfully tested our local username authentication database and our two different users.
To sum up, we learned how to configure a local username/password database in the Cisco IOS. We configured our lines (aux, console, and vty) to use the local database using the login local command. We then used that database for local login authentication. The privilege command can also be used to set privileges for these users. There are many more options for the username and privilege commands. For more information on configuring Cisco IOS usernames, see the Cisco documentation username command reference.
More Cisco Network Tips:
Cisco IOS, How Much You Know About Cisco IOS?